In this post, we will look at a few different tools that we can use to enumerate the MSRPC service running on TCP/UDP port 135.
We will start with a brief introduction on MSRPC as well as a high level overview of how it works.
From there, we will perform an nmap scan on a Windows 10 host and find that the MSRPC service is running.
After scanning the host, we will begin our enumeration of RPC endpoints by querying the RPC locator service with a tool called rpcdump.py. Additionally, we will see how to look for a specific (potentially exploitable) service.
Next, we will search for endpoint mappings using a tool called rpcmap.py. Unfortunately, the Windows 10 host does not allow anonymous access. However, we will pivot our efforts onto the DC where we will have better luck.
Consequently, after dumping the mappings we will find an interesting RPC service running that can be exploited. Using a public exploit, we will extract all of the different interfaces and their assigned IP addresses from the DC.
Once we have extracted the IP addresses, we will find an active IPv6 address assigned to one of the interfaces on the DC. As a bonus. we will see some things we can do and tools that we can use to target the IPv6 address and further our enumeration efforts.
Finally, we will explore four different Metasploit modules that can be used to enumerate MSRPC.
MSRPC (Remote Procedure Call) – Port 135
Microsoft Remote Procedure Call (MSRPC), is a communication protocol that is used to request a service from a program located on another computer in the network. In other words, MSRPC is used to call other processes on remote systems as if they were being called from the local system. This is accomplished using the “client-server” or “request-response” model.
Specifically, an RPC is initiated by the client, which sends a request message to a known remote server to execute a specified procedure with supplied parameters.
If you want to know how RPC works in grater detail, check out the Wikipedia page here.
The RPC endpoint mapper can be accessed through TCP and UDP port 135, through SMB (pipe) using a null or authenticated session (TCP 139 and 445), and as a web service listening on TCP port 593. Additionally, it is common to find RPC ports open on 49xxx, which are known as the “randomly allocated high TCP ports”.
The MSRPC service uses IPC mechanisms, such as named pipes, NetBIOS or Winsock, to establish communications between the client and the server. The IPC$ transport, TCP, UDP, and HTTP protocols are used to provide access to services. This is important to understand when it comes to MSRCP over SMB.
However, for this post we will be focusing on purely port 135 enumeration (as much a possible).
Furthermore, because RPC is used to request remote services from another host in the network, we as attackers should be thinking about how we could potentially pass specially crafted input to an application and execute arbitrary code on the target system.
Initial Enumeration – Nmap Scan
To begin, let’s say that we have a target Windows 10 machine with an IP address of 172.16.1.200 that we just ran a TCP scan against using nmap.
nmap -A -sV -sC -T4 172.16.1.200 -p- -oN tcp_full.nmap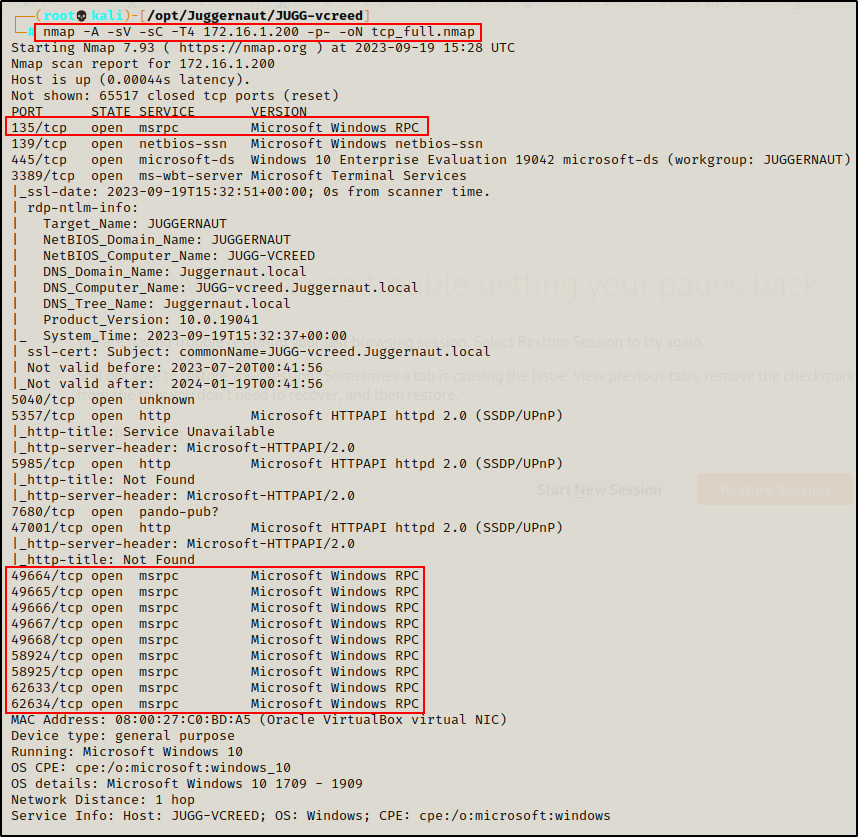
From the output of the nmap scan, we can see that port 135 is open as well as the high RPC ports.
Now that our nmap scan has finished running and we have confirmed that port 135 is open, it’s time to start enumerating this service.
Enumerating RPC Endpoints – rpcdump.py
We can interact with port 135 to query the RPC locator service and individual RPC endpoints. This allows us to catalog interesting services running over TCP, UDP, HTTP, and SMB named pipes.
The RPC locator service is accessed by using four protocol bindings:
- ncacn_ip_tcp — TCP port 135
- ncadg_ip_udp — UDP port 135
- ncacn_http — RPC over HTTP via TCP port 80, 593, and others
- ncacn_np — the \pipe\epmapper named pipe via SMB
ncacn_ip_tcp and ncacn_np are the most common bindings we will find ourselves targeting in our enumeration, but the others are important to understand as well.
The best tool that we can use to remotely query the RPC locator service is rpcdump.py, which is part of the Impacket Collection of Scripts.
This script dumps a list of RPC endpoints and string bindings registered on the target. Additionally, it also tries to match them with a list of well known endpoints.
rpcdump.py 172.16.1.200 -p 135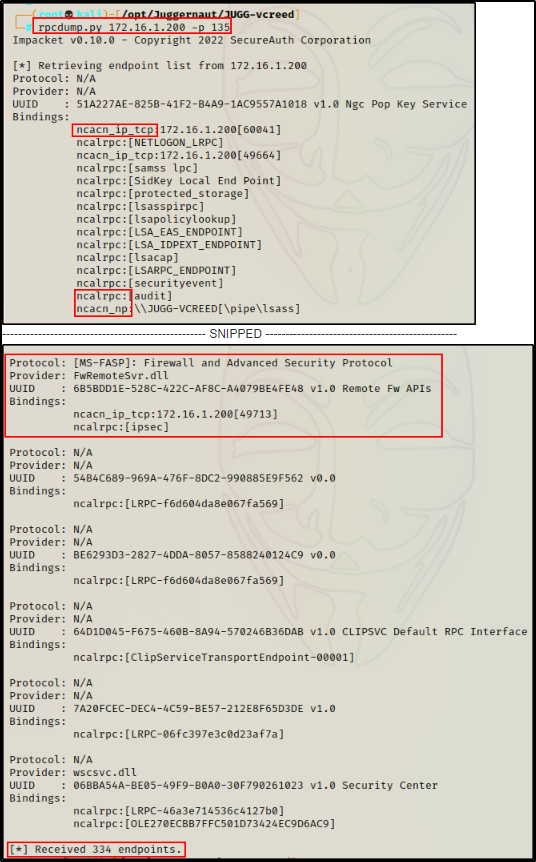
Here we can see that rpcdump.py was able to collect a list of all endpoints, which is a list of services running on the system as well as their bindings. In total, 334 endpoints were dumped (running services) that utilize the endpoint mapper and are assigned an RPC port number.
The RPC endpoint mapper allows RPC clients to determine the port number currently assigned to a particular RPC service. An endpoint is a protocol port or named pipe on which the server application listens to for client remote procedure calls.
Grepping for Interesting Running Services
Because we are actually seeing services running internally, there are some specific ones we can look for that may provide a potential attack vector. For example, we can check if the print spooler service is running – if it is, we may be able to remotely exploit PrintNightmare and get a SYSTEM shell.
rpcdump.py 172.16.1.200 -p 135 | egrep 'MS-RPRN|MS-PAR'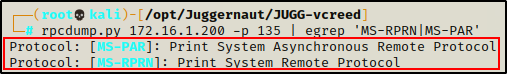
Seeing both of these return a value indicates that this host is likely vulnerable to PrintNightmare!
To learn more about exploiting PrintNightmare, check out my post on the topic here.
Now that we have seen how to remotely dump a list of endpoints on a given host, we can take it one step further and try to uncover some interesting endpoint mappings.
Mapping RPC Endpoints – rpcmap.py
Another tool we can use to enumerate MSRPC is rpcmap.py, which also comes from the Impacket Collection of Scripts.
Rpcmap.py scans for listening DCE/RPC interfaces and binds to the MGMT interface to get a list of interface UUIDs. If the MGMT interface is not available, it uses a list of known interface UUIDs observed in the wild and tries to bind to each interface. As a result, this tool will identify open DCE/RPC interfaces on a target system.
Essentially, where rpcdump.py was able to dump the endpoints and bindings, we can now use rpcmap.py to determine the endpoint mappings.
To begin, we can start by enumerating the mappings on the ncacn_ip_tcp (TCP port 135) binding.
rpcmap.py 'ncacn_ip_tcp:172.16.1.200'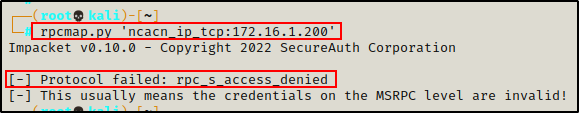
Unfortunately, by default on a domain joined Windows 10 machine, we cannot enumerate endpoint mappings anonymously – we are denied access.
However, the same is not always true for Windows Server machines. Oftentimes, by default they do allow anonymous access on the MSRPC level.
For this reason, we’ll shift our focus on to the Domain Controller to see what we can find with an anonymous session.
rpcmap.py 'ncacn_ip_tcp:172.16.1.5'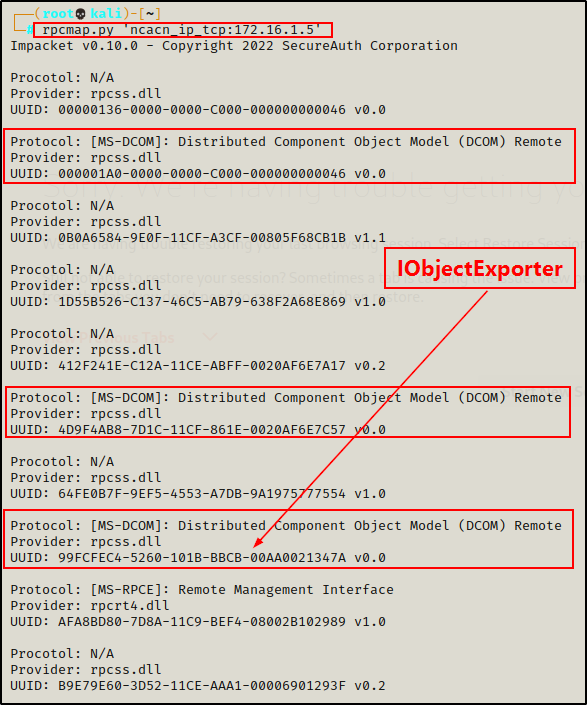
Amazing! We were able to anonymously dump endpoint mappings to find listening RPC services as well as their UUID’s.
After getting these services, we can search online to find if any of them are vulnerable to a remote overflow exploit.
Remote overflow vulnerabilities are more common in older versions of Windows. With that being said, there is a recent one worth knowing about: CVE-2022-26809
There is a site, here that we can use to reference the UUID values to determine their assignments. Specifically, one that we should be particularly interested in is the RPC interface UUID for IObjectExporter, aka the IOXIDResolver (used in potato attacks).
IObjectExporter – {99fcfec4-5260-101b-bbcb-00aa0021347a}
Retrieving Network Interface IPs Through MSRPC
Having found the IObjectExporter service running, we can use a cool trick to extract the IPs from all of the network interfaces on the host. Extracting the network interfaces may reveal additional networks that can be pivoted to, or it may potentially provide an IPv6 address.
If we discover an IPv6 address, we can use it to try and find additional services on the host to enumerate / exploit.
To do this, we need to use a script that can be found here.
After copying the script onto our attacker machine, we can see that all we need to do to run it is use the -t switch followed by the victim IP address.

Finally, all that is left to do is run the script against the DC and extract all of the network interfaces.
./IOXIDResolver.py -t 172.16.1.5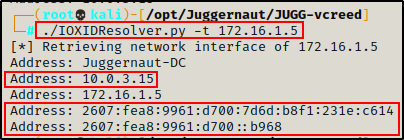
BOOM! Using the script, we were able to uncover an IP from another network – 10.0.3.15. This could be a potential pivot opportunity.
In addition to finding and IP from another network, we also found some IPv6 addresses!
Amazingly, this also worked on the Windows 10 host – even though we were denied access with rpcmap.py

Enumerating Newly Discovered IPv6 Address
To start, we can ping the IPv6 address to make sure that we can communicate with it.
ping -c 3 2607:fea8:9961:d700:7d6d:b8f1:231e:c614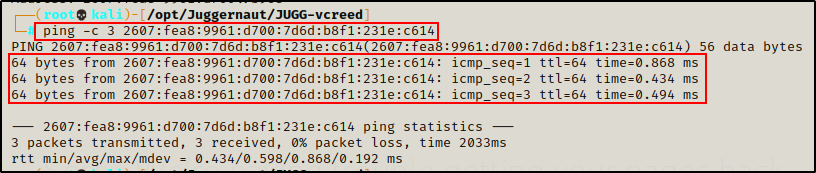
Perfect! The ping was successful.
Next, we should try to find any previously undiscovered open ports using nmap, which supports IPv6 addresses when using the -6 switch.
nmap -6 -A -sV -sC -T4 2607:fea8:9961:d700:7d6d:b8f1:231e:c614 -p- -oN tcp_ipv6.nmapFrom here, we would hopefully find a new interesting service running on IPv6 that we did not find when we enumerated the ports running on IPv4.
For example, if we found port 445 open on IPv6 and not open on IPv4, we can still utilize a lot of the same tools we use when hacking IPv4. This is because a lot of tools have added IPv6 support as it is essential in today’s modern networks.
Some tools that can be used to interact with SMB over IPv6 include smbclient and crackmapexec, just to name a few.
smbclient -L 2607:fea8:9961:d700:7d6d:b8f1:231e:c614 -N
crackmapexec smb 2607:fea8:9961:d700:7d6d:b8f1:231e:c614 --shares -u '' -p ''
Alright, that was cool, but let’s get back on topic.
In addition to Impacket’s rpcdump.py and rpcmap.py, another great tool we can use to enumerate MSRPC over port 135 is Metasploit
Enumerating RPC with Metasploit
Metasploit has some pretty good scripts to accomplish a lot of what we were able to do with rpcdump.py and rpcmap.py, plus more.
To begin, let’s fire up Metasploit with the following command:
msfconsole -qOnce presented with the Metasploit prompt, we can type the following command to see all of the RPC enumeration scripts:
search auxiliary/scanner/dcerpc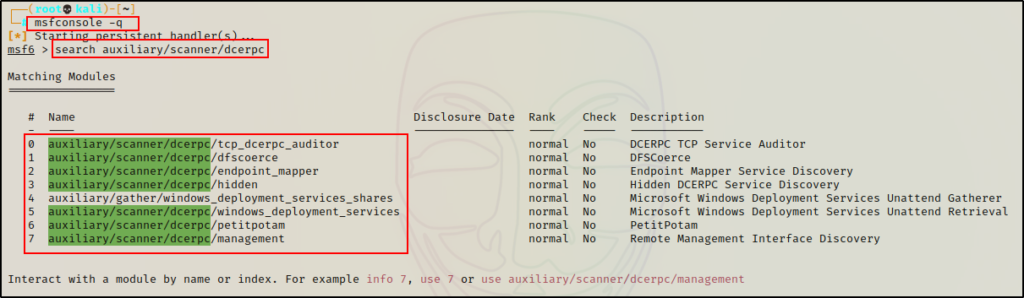
From the search, we are presented with 8 auxiliary modules; however, not all of these will be useful in our enumeration.
For our enumeration, we will focus on the four modules that utilize port 135, which are:
- auxiliary/scanner/dcerpc/endpoint_mapper
- auxiliary/scanner/dcerpc/hidden
- auxiliary/scanner/dcerpc/management
- auxiliary/scanner/dcerpc/tcp_dcerpc_auditor
Moving on, let’s see an example of each of these in action!
auxiliary/scanner/dcerpc/endpoint_mapper
The endpoint_mapper module queries the EndPoint Mapper service of a remote system to determine what services are available. This is similar to when we used rpcdump.py earlier.
use auxiliary/scanner/dcerpc/endpoint_mapper
show options
set RHOSTS 172.16.1.200
exploit
auxiliary/scanner/dcerpc/hidden
This module will query the endpoint mapper and make a list of all ncacn_tcp RPC services. It will then connect to each of these services and use the management API to list all other RPC services accessible on this port.
Any RPC service found attached to a TCP port, but not listed in the endpoint mapper, will be displayed and analyzed to see whether anonymous access is permitted.
use auxiliary/scanner/dcerpc/hidden
show options
set RHOSTS 172.16.1.200
exploit
Here we can see that anonymous access is denied for all of the interfaces tested when targeting the Windows 10 machine.
However, when targeting the DC, some hidden services are discovered.
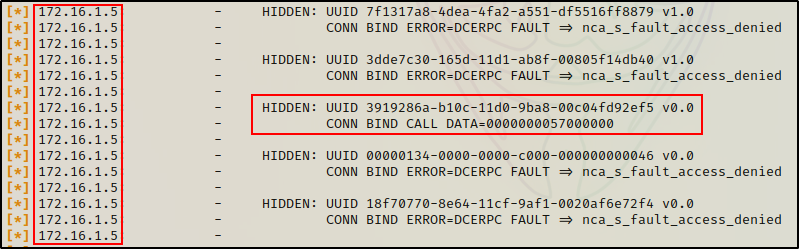
This is cool because it provides us with additional UUIDs that we did not get from dumping endpoints. The hope is that these hidden services map to ones that are vulnerable.
auxiliary/scanner/dcerpc/management
This module can be used to obtain information from the Remote Management Interface DCERPC service.
use auxiliary/scanner/dcerpc/management
show options
set RHOSTS 172.16.1.200
exploit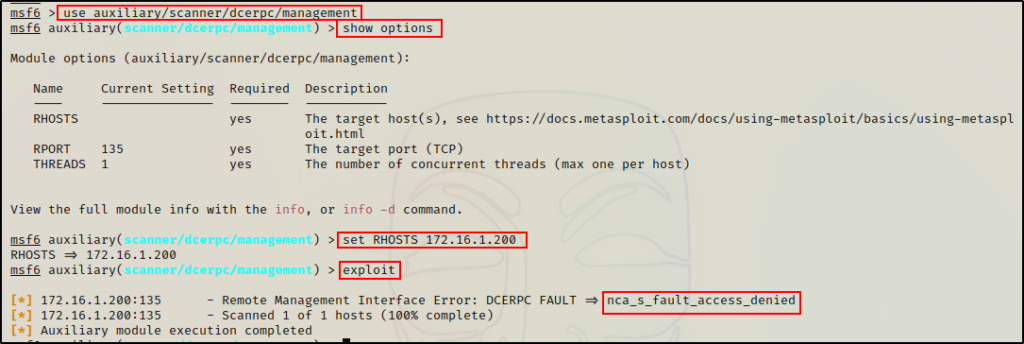
Again, anonymous access is denied when targeting the Windows 10 host.
Alternatively, when targeting the DC we have better luck and anonymous access is accepted.
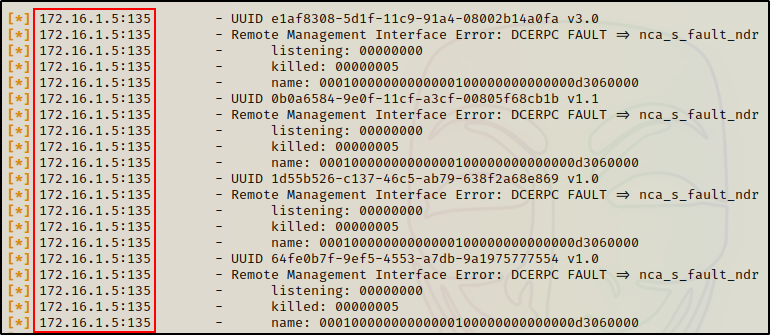
auxiliary/scanner/dcerpc/tcp_dcerpc_auditor
This module allows us to determine which DCERPC services are accessible over a TCP port.
use auxiliary/scanner/dcerpc/tcp_dcerpc_auditor
show options
set RHOSTS 172.16.1.200
exploit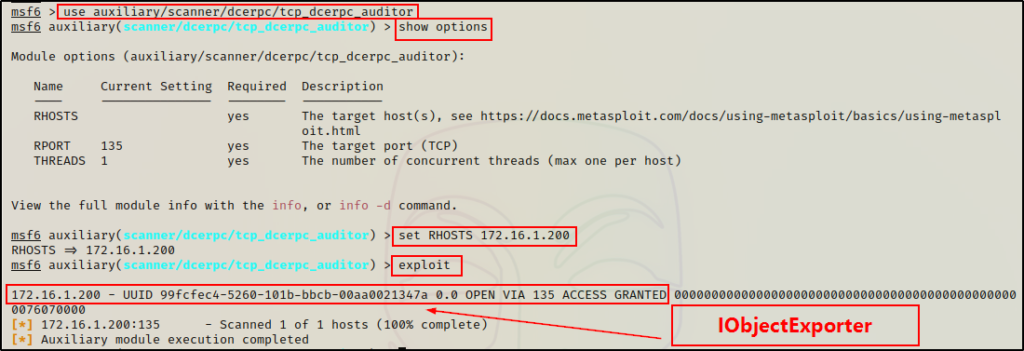
Interestingly, this connects to the IObjectExporter, which is what we found on the DC with rpcmap.py earlier. We then exploited it to extract all of the adapter IPs.
Moreover, this is a good module to use in order to confirm if this service is running when access is denied with rpcmap.py.
Final Thoughts
As you can see, there is some pretty good enumeration that can be done on port 135. A lot can be discovered, and it is definitely not a port that should be overlooked.
We as attackers should always start our enumeration by trying to get anonymous access anywhere we can. When services like MSRPC allow this type of access, it provides a great deal of information that could lead to finding credentials, or even obtaining a foothold on the system.
