In this post we will review how Insecure GUI Applications can be abused to achieve privilege escalation on a Windows target.
We will start by finding a shortcut to an application on the desktop that we will execute. Once executed, we will check the running processes to find that the application is running as Administrator. From there, we will break out of the application into an Administrator shell. As a bonus, we will also review another GUI application that can be abused in a similar fashion named hhupd.exe.
Windows applications can be configured such that users could are granted permissions to run a certain GUI application with Administrator privileges. This is often necessary when the program requires elevated permissions to perform some of its functions.
Finding an Application that Runs as Administrator
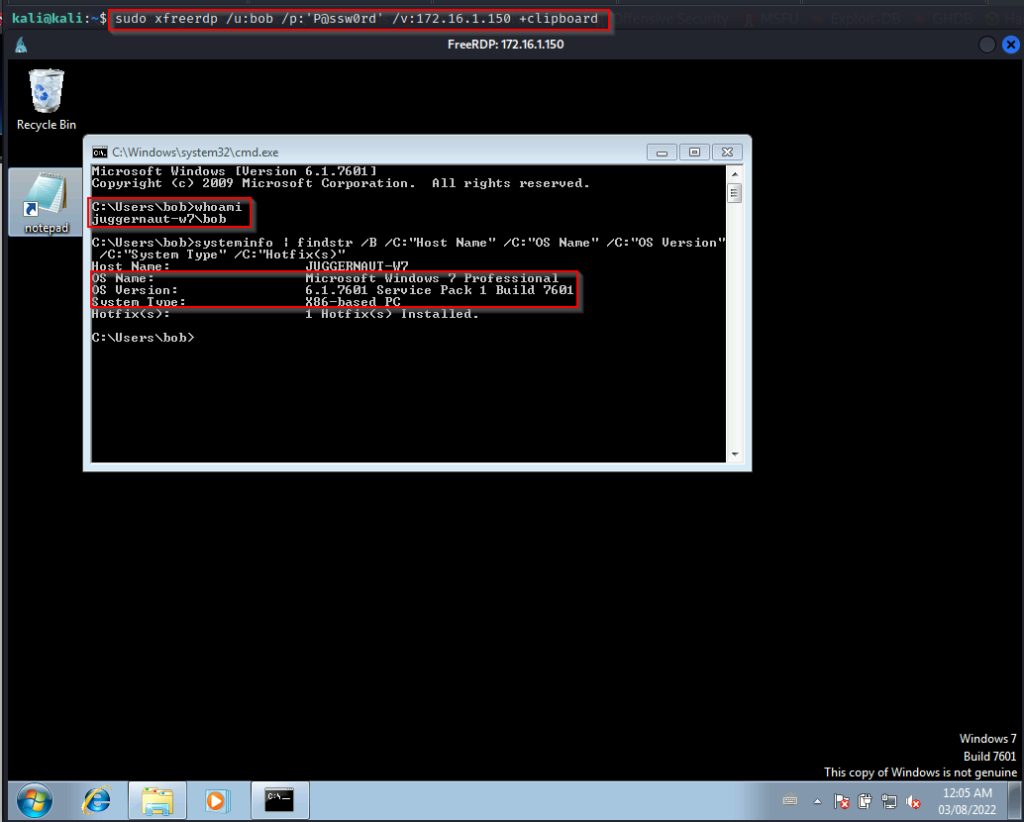
Since the examples in this post require GUI, let’s say that during our initial enumeration we found credentials for the user bob and that RDP was open on port 3389. We put 2 + 2 together and then logged in using xfreerdp.
sudo xfreerdp /u:bob /p:'P@ssw0rd' /v:172.16.1.250 +clipboard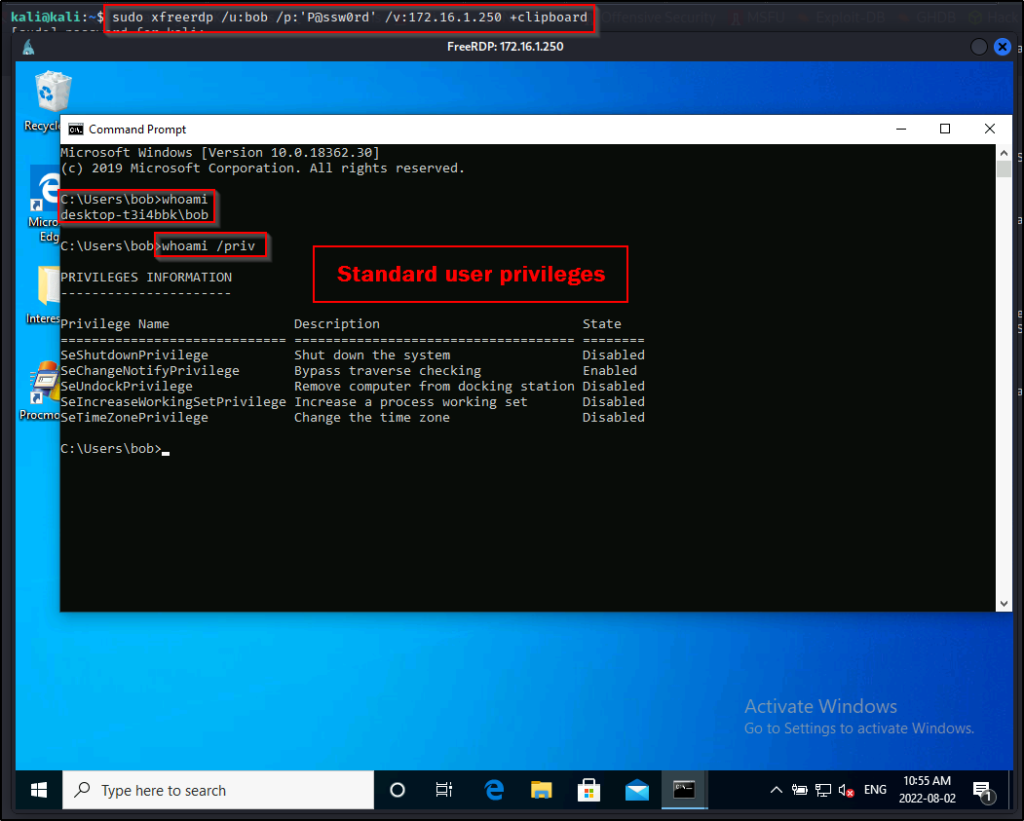
Now that we have gotten a foothold on the target with an RDP session, we can begin by checking out applications on the user’s Desktop.
Here we can see that Procmon is on the Desktop, which may be of interest to us. Additionally, it is known that this program needs to run with admin privileges to be able to view all processes.

We can test if this program runs with Administrator privilege’s by executing it and then checking the running processes using the tasklist command or by checking the Task Manager.
After starting the program, we can use the following command to see what privilege level the program is running with:
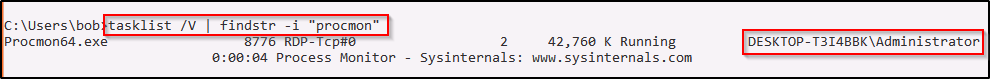
tasklist /V | findstr -i "procmon"BOOM! We can see here that the program is running as the local administrator!
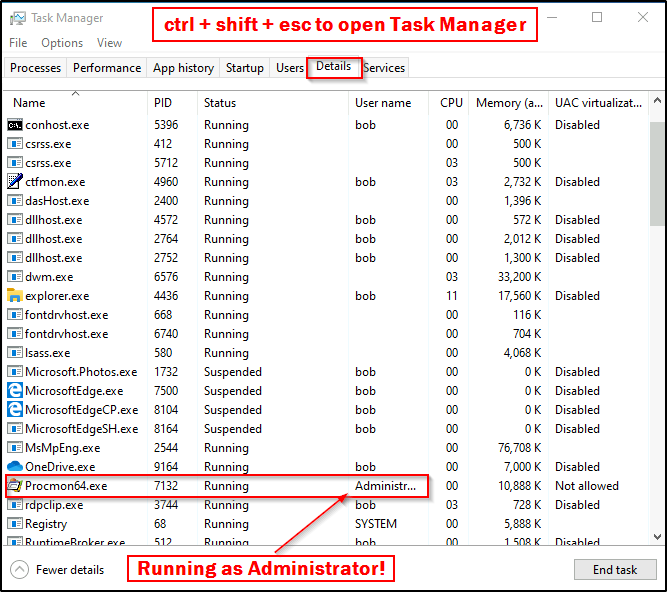
Similarly, since we have GUI access, we can utilize Task Manager to find this information. Start by pressing CTRL + SHIFT + ESC to open Task Manager and then head over to the details tab. Here we can see the Procmon process running as Administrator!
Amazing! We can see that the program is running as Administrator, but how can we abuse this? — Easy, we can just simply “open” a cmd.exe prompt and break of the application!
Breaking Out of an Insecure GUI Application into an Administrator Shell
There are often numerous ways to spawn command prompts from within GUI apps, but our focus will be using native Windows functionality (living off the land). Since the parent process (Procmon application) is running with administrator privileges, we will be able to spawn a command prompt that will also run with the same level of privileges.
Depending on the application that is running, we may get lucky and find that it has an “open” feature to open a file. Fortunately for us, Procmon has this!
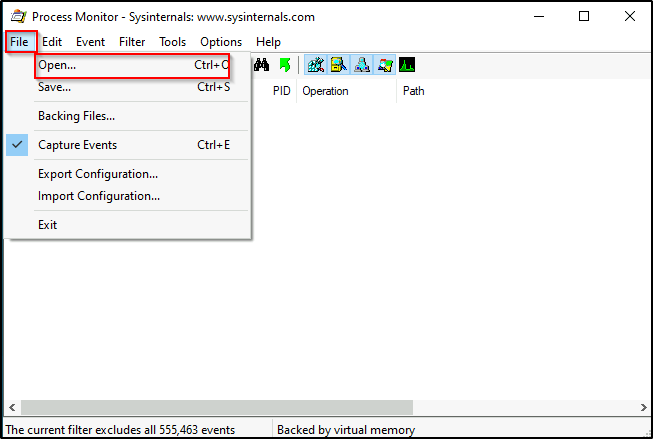
Once we have clicked open, we will be presented with another window to browse for files.
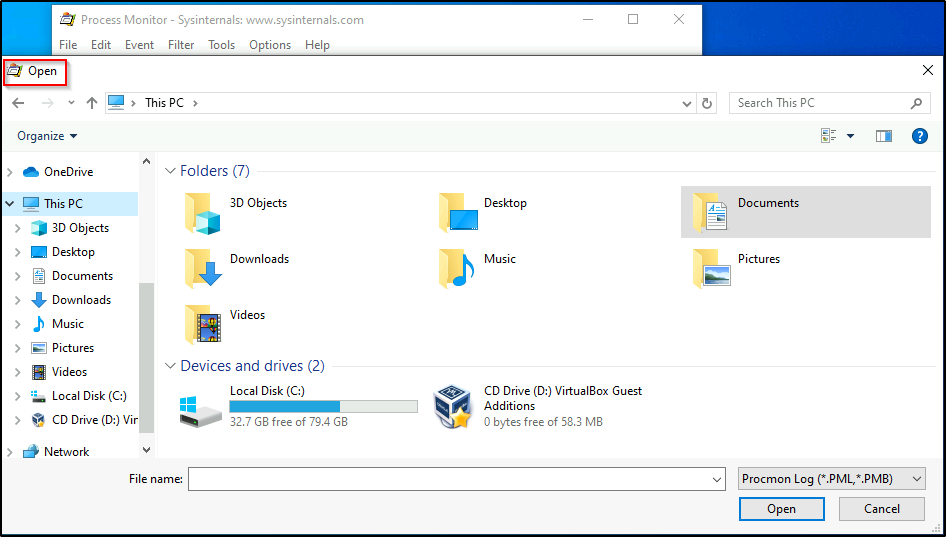
Now for the fun part! We can simply just type in the TOP search bar (not the filename search bar) “cmd.exe” and then press enter.
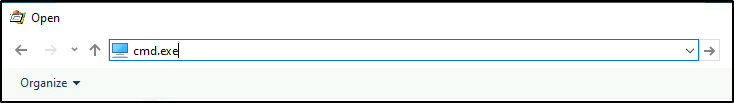
This should open a new command prompt under the context of the user who the application is running as, which in this case is the Administrator!
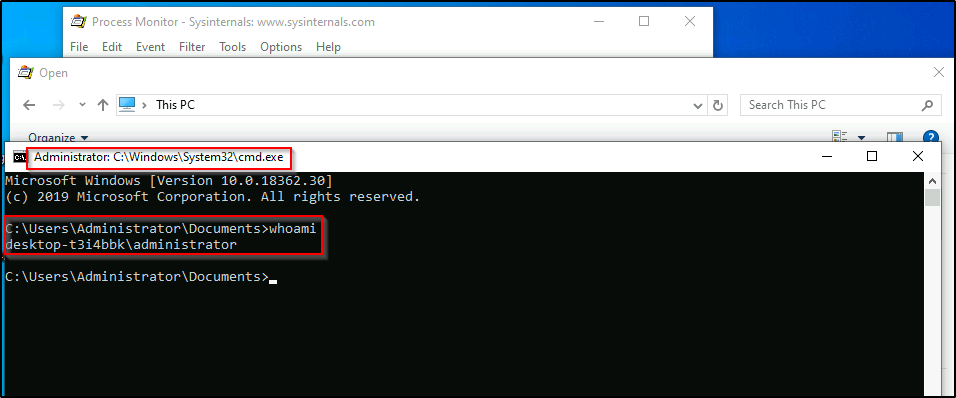
And then we can confirm that this is a high-integrity shell by using the whoami /priv command.
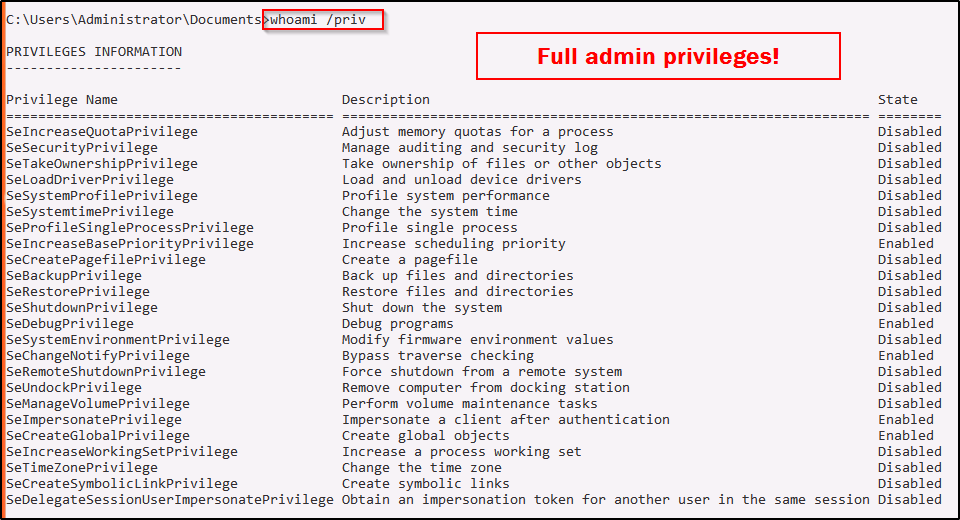
Incredible! Since the application runs as administrator, we found ourselves able to break out of the application into an Administrator shell!
CVE-2019-1388 – hhupd.exe Case Study
For this example, we will say that we have GUI access to a Windows 7 machine as standard user bob the same way we did earlier on the Windows 10 machine.
There is a privilege escalation vulnerability in the Windows Certificate Dialog (hhupd.exe) that allows an attacker to elevate privileges to SYSTEM and has been documented as CVE-2019-1388.
hhupd.exe is known as HTML Help 1.32 Update and it is developed by Microsoft Corporation.
This CVE affects a lot of Windows versions including Windows 7, 8, 10 up to version 1903, and server 2008 – 2019 up to version 1903. A detailed list of affected versions can be found below.
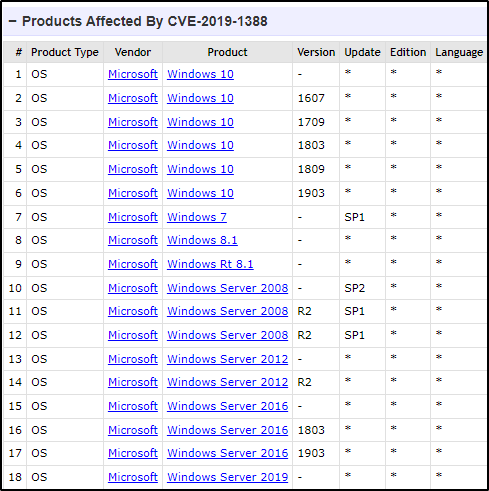
Alright, now that we know which versions of Windows are vulnerable, let’s see how this exploit works on a Windows 7 victim.
In my experience, this exploit requires Internet Explorer to be the default browser.
If hhupd.exe is not already on the victim system, which it will NOT be by default, then we can download a copy of it onto our attacker machine from here.
After downloading the file onto our attacker machine, we need to move it to a working directory and then setup and HTTP server so that we can download it onto the victim.
python3 -m http.server 80
Now we can simply navigate to our web server using IE from the RDP session and then download hhupd.exe onto the victim desktop.
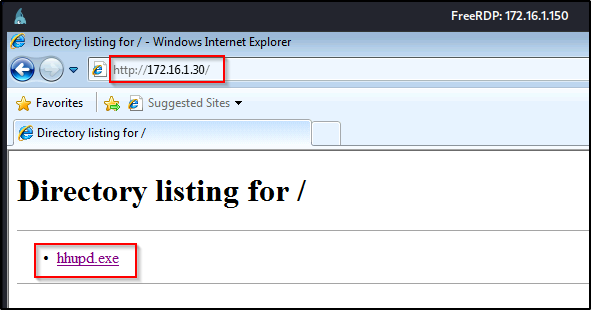
After saving the file to the Desktop, it should now be visible, like so:
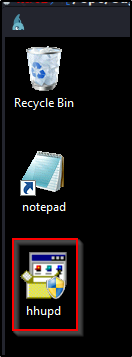
Now for the fun part! For this to work, we need to close IE and then when we perform the exploit, it will spawn a new instance of IE as SYSTEM!
Now that IE has been closed, right-click the hhupd application and select Run as Administrator.
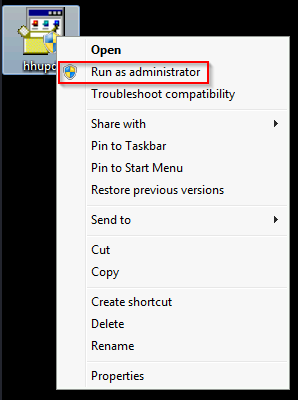
But wait… we are not admin and don’t know the password to get past the UAC prompt!? That’s just thing about this exploit, it doesn’t matter that we are not admin as we will still be able to bypass UAC and get a SYSTEM shell!
Even though we are using UAC as a means to elevate to SYSTEM, this is technically not “UAC Bypass”. To learn more about UAC Bypass techniques, check out my post on the topic here.
After clicking Run as Administrator, go to show more details and then click show information about publishers certificate when it comes up.
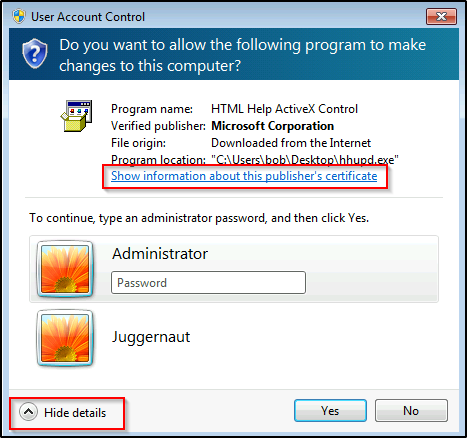
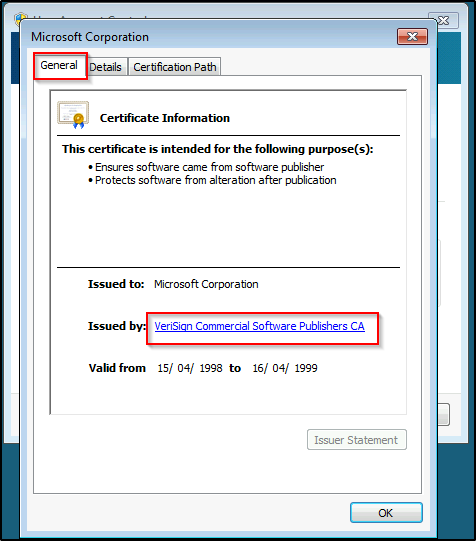
Alright, now this is where the vulnerability exists. When we click on the cert that was issued, it opens up IE as SYSTEM!
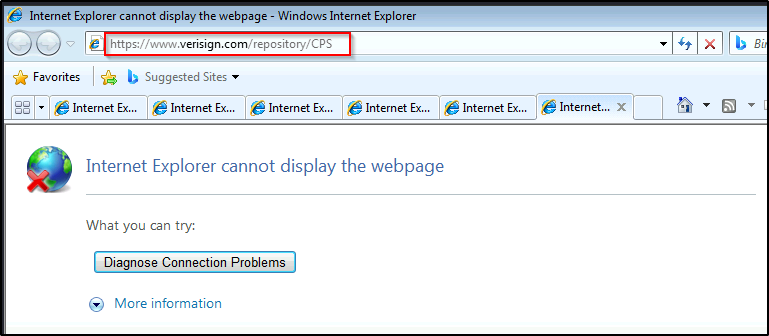
Rapid-fire click the link a few times and then hit “OK” and then “No” to the UAC prompt. We should see that IE has spawned and is trying to get to the VeriSign website.
Now all we have to do is simply click the Page button and then click Save As…
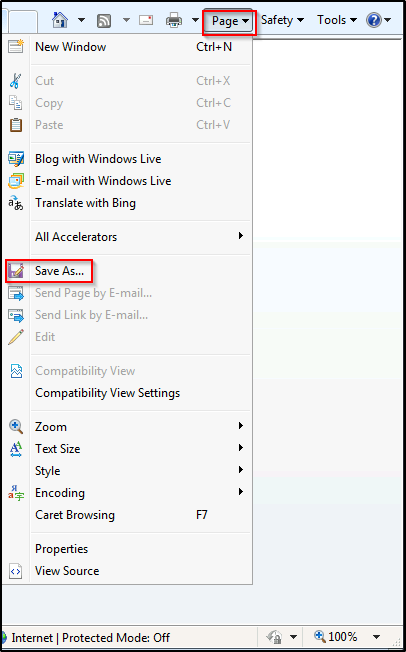
On Windows 10 there is a gear icon that has replaced the “Page” tab.
Just like we saw earlier with the Procmon breakout, we just need to type “cmd.exe” in the TOP search bar and it should break out of IE and spawn a SYSTEM shell.
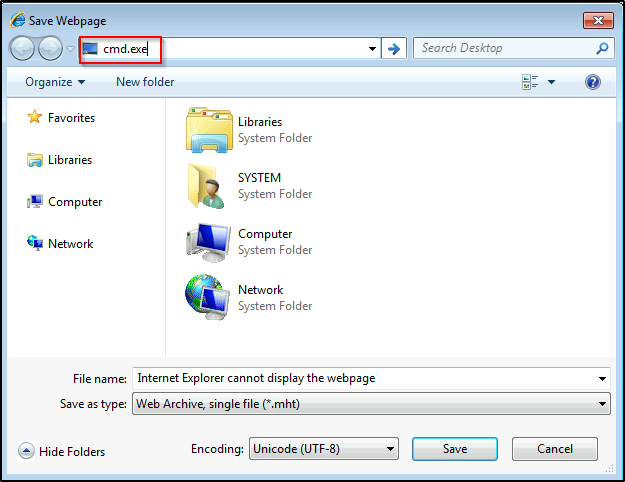
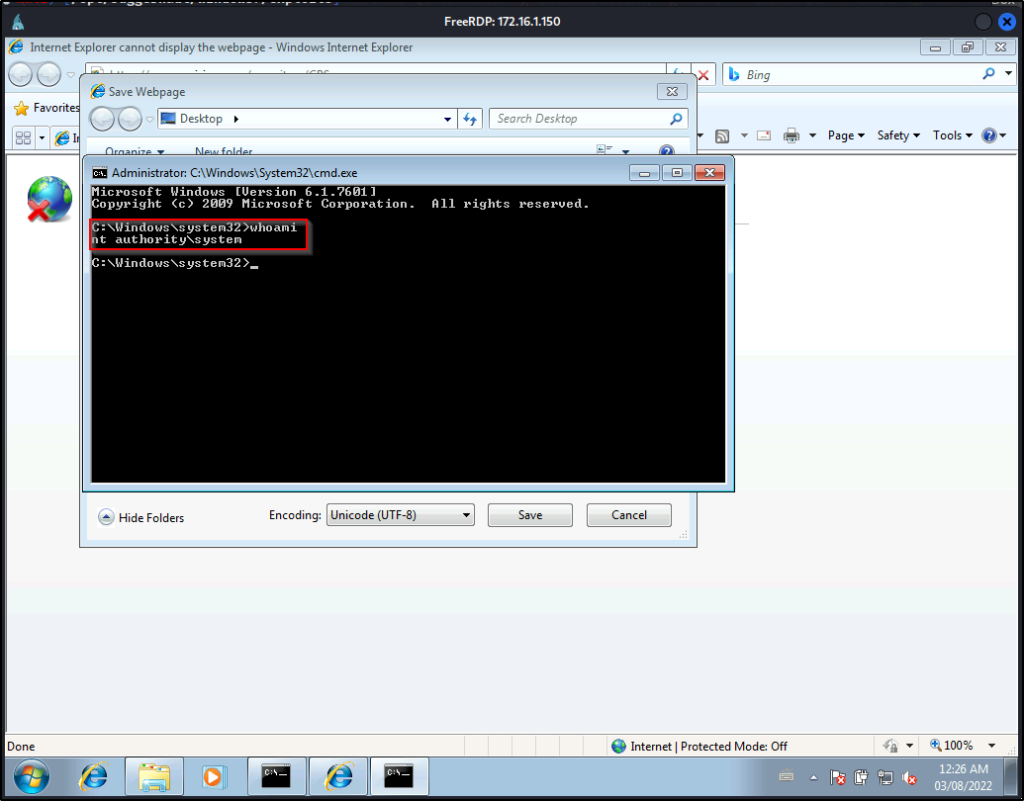
BOOM! Just like that we abused the GUI application to elevate our privileges to SYSTEM!
