NFS Share no_root_squash – Linux Privilege Escalation
In this post, we will learn how to enumerate and attack an NFS share in order to elevate our privileges from a standard user to root. We will start by enumerating open…

In this post, we will learn how to enumerate and attack an NFS share in order to elevate our privileges from a standard user to root. We will start by enumerating open…
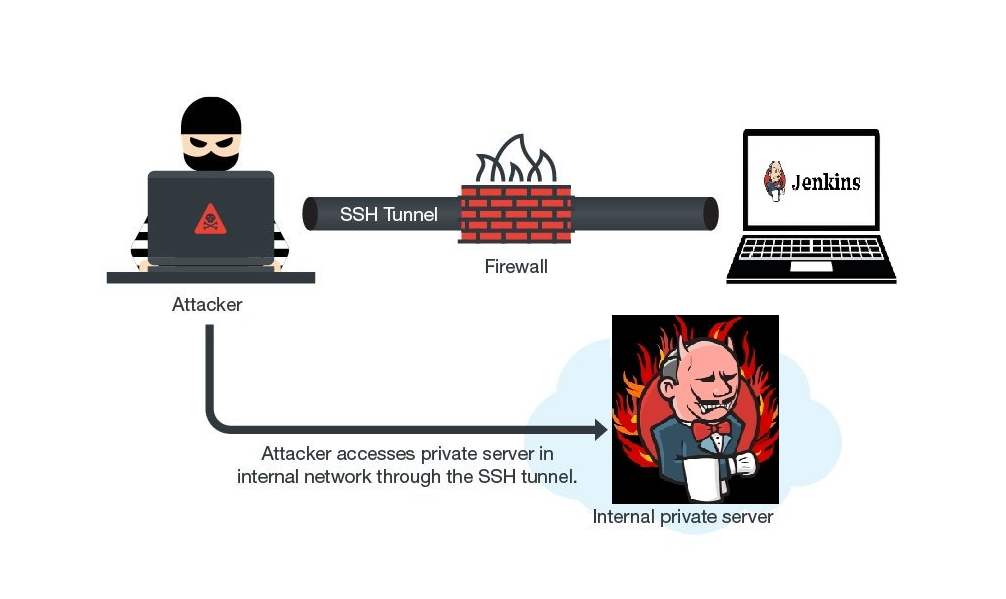
In this post we will be exploring a Linux privilege escalation technique know as port forwarding. Port forwarding is a technique that allows an attacker to directly access internal or firewall blocked…
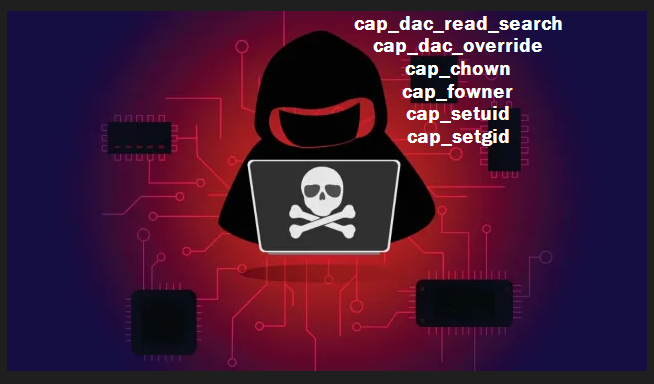
In this post, we will perform a deep-dive on how to exploit various capabilities. Specifically, we will see how six different capabilities can be leveraged by an attacker (that’s us!) to obtain…

In this post we will learn how to elevate our privileges on a Linux target by abusing User Defined Functions (UDF) in MySQL. By discovering a few bad configuration choices and locating…

In this post we will be exploring various kernel exploits that can be used for Linux Privilege Escalation from standard user to root. We will start by using various commands to find…

In this post we will be exploring manual enumeration techniques that can be used to get a “lay of the land” on the target once a foothold has been established. Manual enumeration…

In this post we will review how Insecure GUI Applications can be abused to achieve privilege escalation on a Windows target. We will start by finding a shortcut to an application on…

In this post we will cover the topic of AppLocker Bypass, which can be considered a step towards Windows Privilege Escalation because AppLocker will stuff all of our attempts to execute any…

In this post we will be going over Windows Subsystem for Linux (WSL) and how it can be exploited as a potential means for privilege escalation. We will obtain a foothold on…