Password Hunting – Windows Privilege Escalation

In this post we will be exploring the art of password hunting on a target machine as a means to escalate privileges either horizontally or vertically. We will go over various different…

In this post we will be exploring the art of password hunting on a target machine as a means to escalate privileges either horizontally or vertically. We will go over various different…

Continuing with Windows Privilege Escalation techniques, in this post we will be covering the concept of DLL Hijacking. We will be focusing on two different types of DLL hijacking, which can both…

In this post, we will be deep-diving into various attacks that we can use against an MSSQL server. From these attacks, we will learn how this service can be leveraged for Windows…

For this post on Windows Privilege Escalation techniques, we will be exploring vulnerable scheduled tasks. Similar to many of the Windows privilege escalation techniques we have gone over in other posts, this…

For this post, we will be exploring another service vulnerability that involves weak permissions; however, instead of the service itself containing weak permissions, we will find that the folder housing the service…

For part 2 of this post we will be shifting our focus to kernel exploits for modern Windows operating systems, which include Windows versions Windows 10 and Server 2016 In part one…

Due to the volume of information on kernel exploits I have for you guys, this post will be split into two parts. In the first part, we will be learning how to…
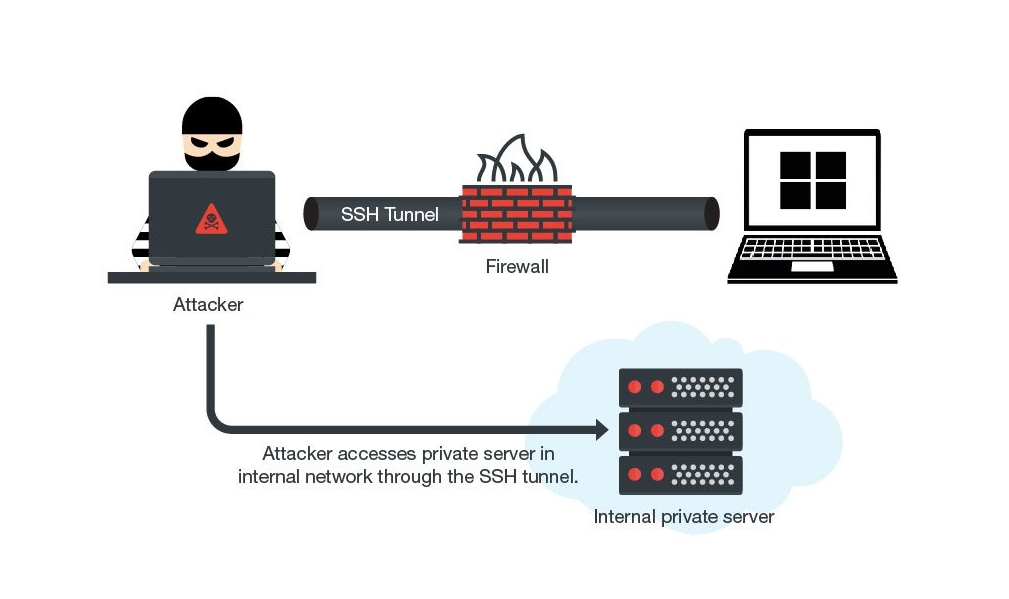
In this post we will be exploring a Windows privilege escalation technique know as port forwarding. Port forwarding is a technique that allows an attacker to directly access internal or firewall blocked…

In this post we will be exploring yet another technique that involves weak permissions; however, instead of a folder / file misconfiguration, this time we will be exploiting weak service permissions. We…